Short bio
Mobile ransomware uses scare tactics to pressure victims into paying fees to unlock their mobile device and restore lost data.
History
Ransomware has long been used on PCs, but it wasn’t until the height of the infamous ransomware Cryptolocker and other similar ransomware in 2014 that ransomware started being seen in large scale on mobile devices.
Common infection method
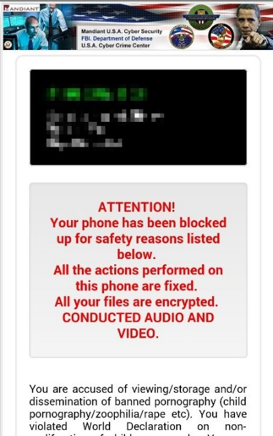
Mobile ransomware locks the mobile device and displays a message that the device has been locked due to some type of illegal activity. The message states that the phone will be unlocked after a fee is paid.
Associated families
- Trojan.Koler
- Trojan.LockScreen
- Trojan.SLocker
- Trojan.SimpLocker
- Trojan.Ransom.TLock
- Trojan.Ransom.Jisut
- Trojan.Ransom.Lipbro
- Trojan.Ransom.Pletor
- Trojan.Ransom.Rivls
- Trojan.Ransom.Roop
- Trojan.Ransom.Small
- Trojan.Ransom.Svpeng
Remediation
Due to the fact that the mobile device is locked, many times the device must be booted into safe mode (consult your mobile device manufacturer with model type for instructions) where only system apps are started on the device at boot. Once in safe mode, these apps can be uninstalled using the mobile device’s uninstall functionality.
Also note that sometimes the ransomware is originating from your mobile device’s web browser, and not from a malicious app installed on the phone. In these instances, simply back out of the offending web page.
Aftermath
Victims who pay the fee often do have their device unlocked, but it’s not guaranteed. In rare cases where the phone does not have a safe mode and the fee is not paid, data stored on the phone could be lost.
Avoidance
Stick to trusted sources for mobile apps and avoid any third party apps.
Screenshots