Unfortunately, scams are a fact of life online. The virtual ties that bind us are international now: Our public telephone numbers, social media accounts, email addresses, messaging apps, dating profiles, and even our physical mailboxes, can all be reached by any criminal and con artist from anywhere in the world.
And test us they do, with everything from the preposterous offers of “Nigerian princes” to the slow boiling intimacy of long-term, long-distance romances.
There is a lot of good advice around (and plenty of it on this website) to help you understand which scams are popular right, how they work, and how to spot them.
Though undoubtedly useful, the advice is often specific to a single campaign or type of scam: Watch out for fake DHL emails; Beware of SMS messages from the Royal Mail; Don’t open invoices from unknown senders; Check the spelling and links in emails; Reverse image search too-good-to-be-true dating profile pics, and so on.
Being specific, the advice is narrow. SMS scams are not the same as email scams, and neither has much in common with a romance scam. There is a lot to remember.
So today I’m going to offer you something different. I want to give you the most general advice I can—a template that can be applied to almost any scam, over any media, on any time scale, whether it’s a new scam or something tried and tested.
It doesn’t make the other advice redundant, it’s just another way to look at things.
The advice comes from perhaps the most famous conman in the world, Frank Abagnale, whose alleged exploits were made famous by Leonardo DeCaprio in the movie “Catch me if you can”. Abagnale’s account of his own backstory is either true, partially true, or a total fabrication, depending on who you ask. What isn’t in doubt is that he knows a thing or two about lying to get what he wants.
In 2019 he gave an interview to CNBC in which he gives perhaps the best generalised advice about scams I’ve ever heard, and which I will repeat here.
In every scam no matter how sophisticated or how amateur, there are two red flags.
These are Abagnale’s red flags:
An urgent need for money
The end goal of all scams is to enrich the scammer. And that often involves a direct transfer of money, whether it’s entering credit card details into a fake website or wiring tens of thousands of dollars to a stranded lover.
The demand for money is almost always urgent. Scammers know that their requests don’t stack up, so they want you to rush, and they don’t want you to involve other people.
In a romance scam where the criminal hopes to make the victim fall in love with them, the scammer may take their time to begin. However, when the demand for money comes, it is likely to be urgent.
On a recent Lock and Code podcast, Cindy Liebes, Chief Cybersecurity Evangelist for the Cybercrime Support Network, spelled out just how patient these scammers can be:
“It can take months, it can take years, but invariably they will seek to get money.”
In other situations, such as business email compromise (BEC) scams, the urgency is immediate.
In a BEC scam an attacker spoofs the email account of a senior employee, such as a CEO, and tries to get a more junior employee to send them some of the company’s money.
Requests often come with a deadline and a demand for secrecy. The “CEO” concocts a story with one or more emails, messages or phone calls about needing help with an urgent, confidential deal. The scammer wants to isolate the employee from the company’s checks and balances, and their own common sense.
Underpinning it all is Abagnale’s first red flag: An urgent need for money.
Sometimes victims aren’t told to act urgently, they just want to. A few months ago we covered an Instagram scam in which victims thought they’d stumbled upon a website where they could see naked pictures of an attractive friend.
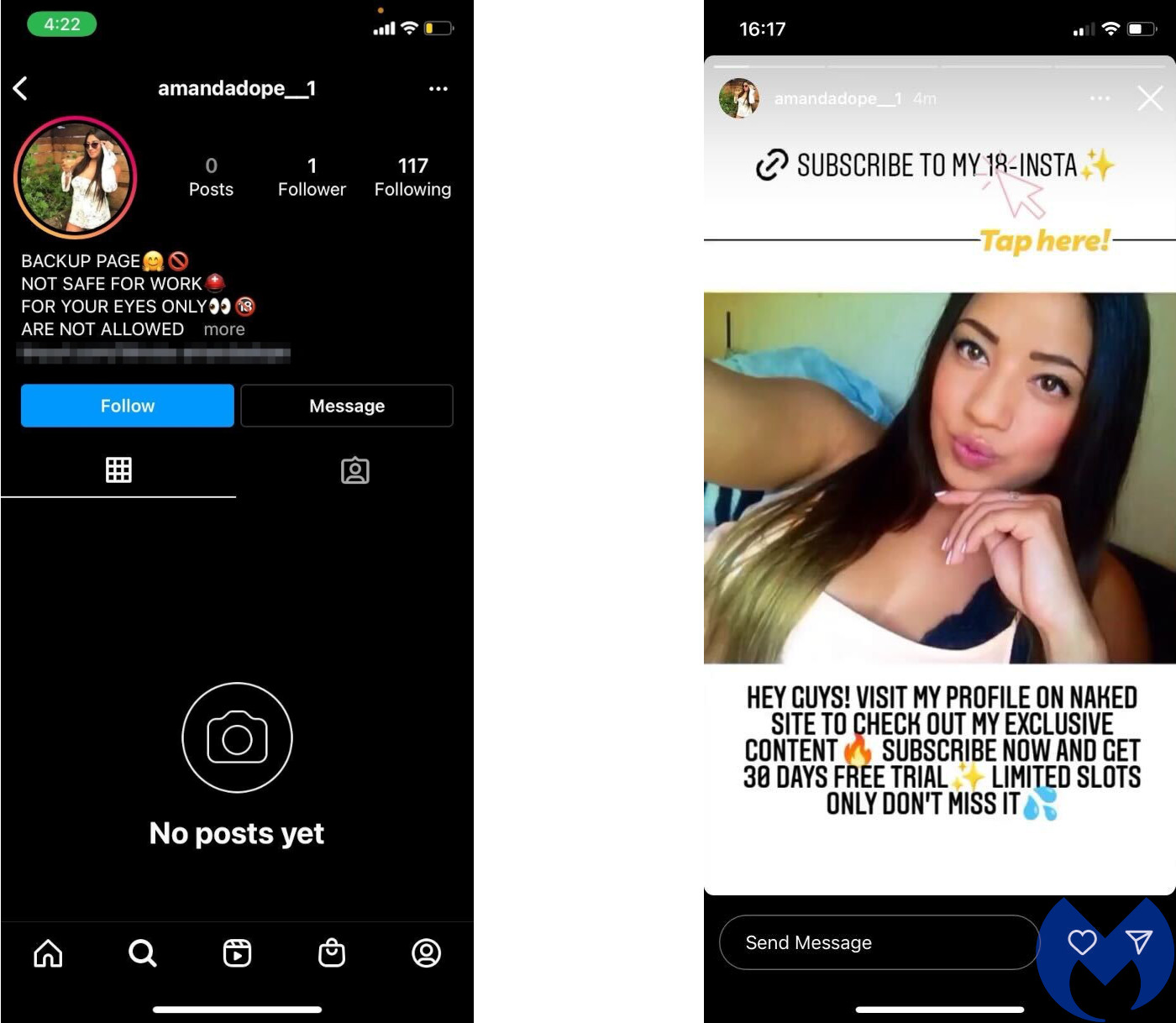
The urgency here came from the viewer’s desire to act on a sexual impulse, and is reinforced by language like “LIMITED SLOTS ONLY, DON’T MISS OUT” and “What are you waiting for?”
The small print even explained the scam in plain terms—victims were being signed up for a premium rate subscription service—but the scammers were betting that victims would be in too much of a hurry to read it.
Asking for personal information
Abagnale’s second red flag is being asked for personal information. Personal information helps the scammer pretend to be you.
Sometimes it’s as simple as stealing your username and password with a fake website, so they can log in as you on the real website.
But it can also be very subtle. In his book The Art of Deception, infamous social engineer Kevin Mitnick describes how he would sometimes make several phone calls to build up the information he needed for a scam.
Each call would capture small details that improved his credibility for the next one. For example, one of Mitnick’s most famous crimes is stealing the source code for a popular Motorola phone in the early 1990s, an attack he described to Vice in 2019.
The attack began with a call to the main Motorola reception, which sent him back-and-forth on several more calls in which he learned the phone number of the VP of Motorola mobility, and that the company had a research centre in Arlington Heights.
This information allowed him to call the VP and credibly introduce himself as “Rick, over in Arlington Heights”, which was enough to convince them to give him the name and phone number of the phone’s project manager.
Mitnick then called the project manager and learned from her voicemail that she was on holiday, and who to contact while she was away. He called the project manager’s stand-in and convinced her that the project manager had not fulfilled a promise to send him the source code before she left on holiday.
Most of the conversations did not ask for enough sensitive information to alert the people he was talking to, but every one of them contained a request for something personal or privileged. Of course, when he finally asked for the source code, he was making a request for hugely privileged information, but he was able to create a plausible enough persona to pull it off.
In fact, the last victim was so convinced of “Rick”’s authenticity that she persuaded a security manager to hand over a username and password for the company’s proxy server, on his behalf.
Thankfully, most of us aren’t faced with a hacker as skilled as Mitnick, and few of us would be able to stop him if we were. Most cons are simpler, more direct versions of the same basic idea.
And that brings me to my final point.
Many scammers are professional criminals and scams are common because they work. It makes sense to prepare yourself as thoroughly as you can to spot them, but we all fall short sometimes. There is no shame in falling for a scam, and it isn’t your fault if you do.










