RoughTed is a large malvertising operation that peaked in March 2017 but has been going on for at least well over a year. It is unique for its considerable scope ranging from scams to exploit kits, targeting a wide array of users via their operating system, browser, and geolocation to deliver the appropriate payload.
We estimate that the traffic via RoughTed related domains accumulated to over half a billion hits and was responsible for many successful compromises due to effective techniques that triage visitors and bypass ad-blockers.
The threat actors behind RoughTed have been leveraging the Amazon cloud infrastructure, in particular, its Content Delivery Network (CDN), while also blending in the noise with multiple ad redirections from several ad exchanges, making it more difficult to identify the source of their malvertising activity.
Highlights
- Traffic comes from thousands of publishers, some ranked in Alexa’s top 500 websites.
- RoughTed domains accumulated over half a billion visits in the past 3 months alone.
- Threat actors are leveraging fingerprinting and ad-blocker bypassing techniques upstream.
- RoughTed can deliver a variety of payloads for each platform: scams, exploit kits, and malware.
Campaign identification
While studying the Magnitude exploit kit, we came across an interesting redirection chain from a domain name called roughted[.]com, hence the nickname ‘RoughTed’ we gave to this campaign.
roughted.com/?&tid=645131&red=1&abt=0&v=1.10.59.18

This domain was calling out to an XML feed to serve ads, but because of our geolocation at the time (South Korea), we were redirected to the Magnitude exploit kit via its pre-filtering gate, also known as ‘Magnigate’.
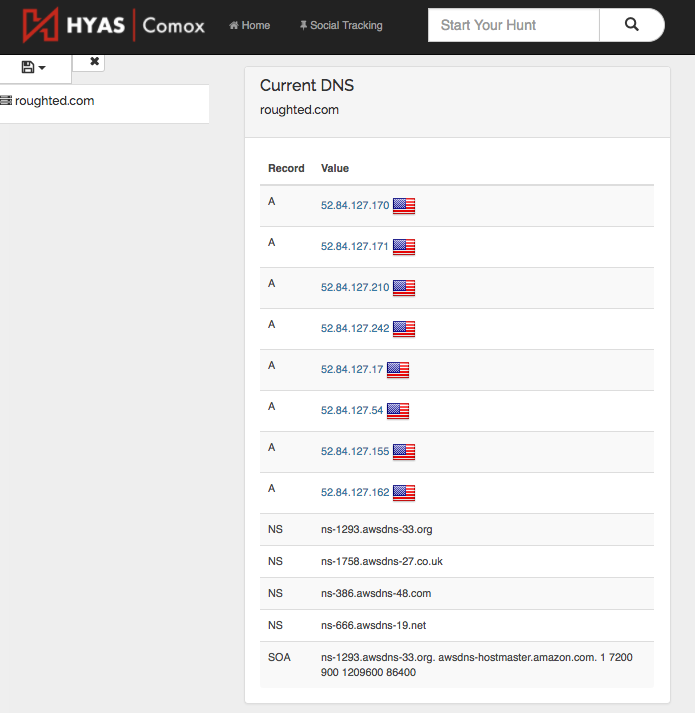
Over the course of a few days, we noticed a similar referer as roughted[.]com, with the same URL structure redirecting to the RIG exploit kit this time. Upon mining our data set, we started seeing that pattern for over a hundred other domains and mapped out some of the most prolific ones.
The majority of the domains were created via the EvoPlus registrar in small batches with a new .ru or .ua email address each time. Another thing in common that these domains have is that they are being used as a gateway meant to bypass ad-blockers (we will expand on that aspect later).
The visualization below shows clusters representing domain names assigned to a unique registrant email.
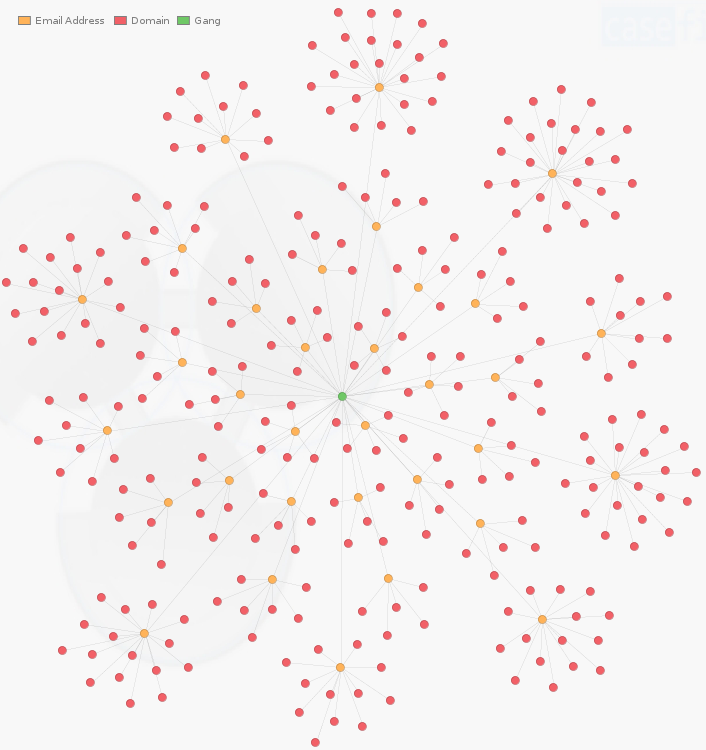
Within each cluster, we can see that the domain naming convention follows a certain pattern, with one or two strings being used in various positions. For example, below we have the strings ‘get‘ and ‘fun‘ used to build the domain name.
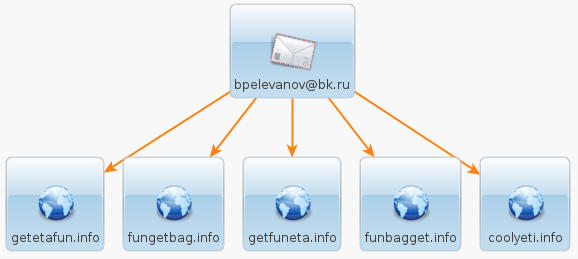
This is in itself is not shocking (it could simply be a lack of imagination) but it becomes interesting when two separate clusters are semantically related (different registrant email but similar domain names). This allows us to connect the campaigns together in yet another way (besides the URI patterns).
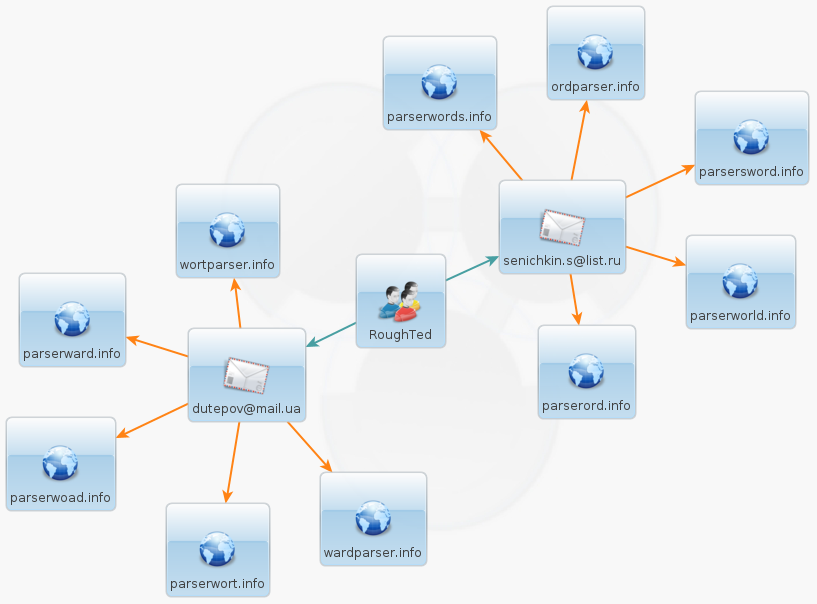
For instance, let’s zoom in on two clusters that show different email addresses. We see that the common string here is ‘parser‘ used in both and it is not just a ‘coincidence’.
Publishers
The term ‘publisher’ is commonly used in the advertising industry to refer to websites that display adverts to generate online revenues. Publishers are typically providers of content (news, media files, etc.) which drive people to visit them regularly. The cost of advertising is not only dependent on how popular a website is, but also on other variables which revolve around the kind of audience a publisher captures.
The bulk of the traffic for the RoughTed campaign comes from streaming video or file sharing sites closely intertwined with URL shorteners. These are areas where malicious actors love to lurk because of the sheer volume of traffic but also subpar standards for quality and safety of online advertising.
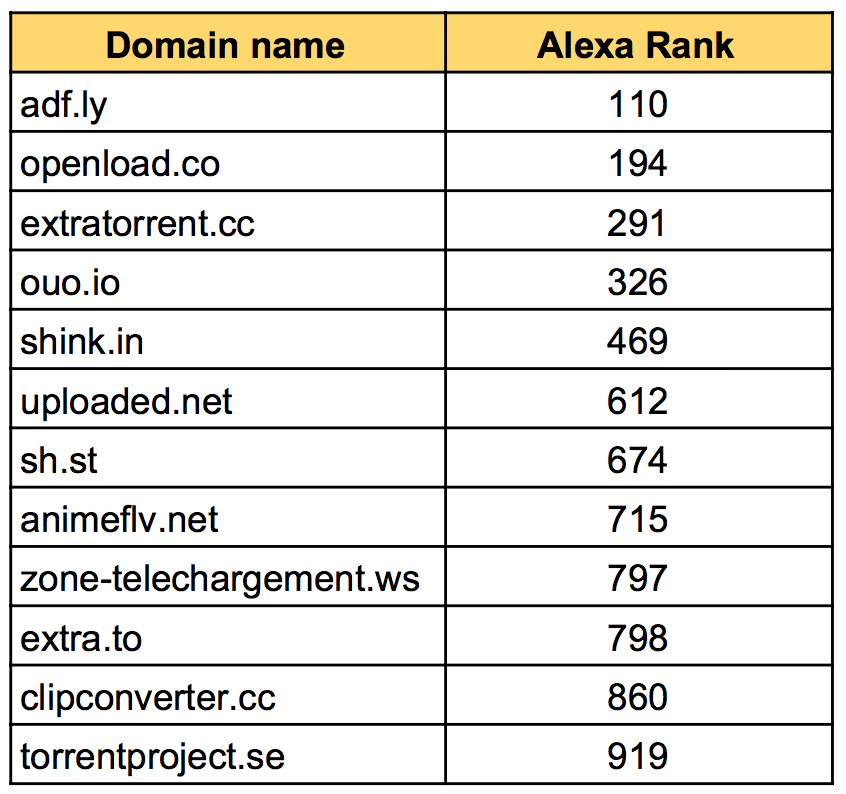
Below are some domains we spotted in our telemetry, ranking within Alexa’s top 1000. Visitors to these sites are targeted with ads and in some cases, some that belong to the RoughTed campaign. We will detail later to what kind of content users were exposed.
During our research, we spoke with Denis Sinegubko from website security company Sucuri who shared similar findings with how ‘personal’ websites were involved in this malvertising campaign. Webmasters knowingly integrated an ad code script from advertising company Ad-Maven into their pages in order to monetize their website.
[Edit 06/06/17] Note: Ad-Maven simply provides the technology and is not the cause of this malvertising campaign.
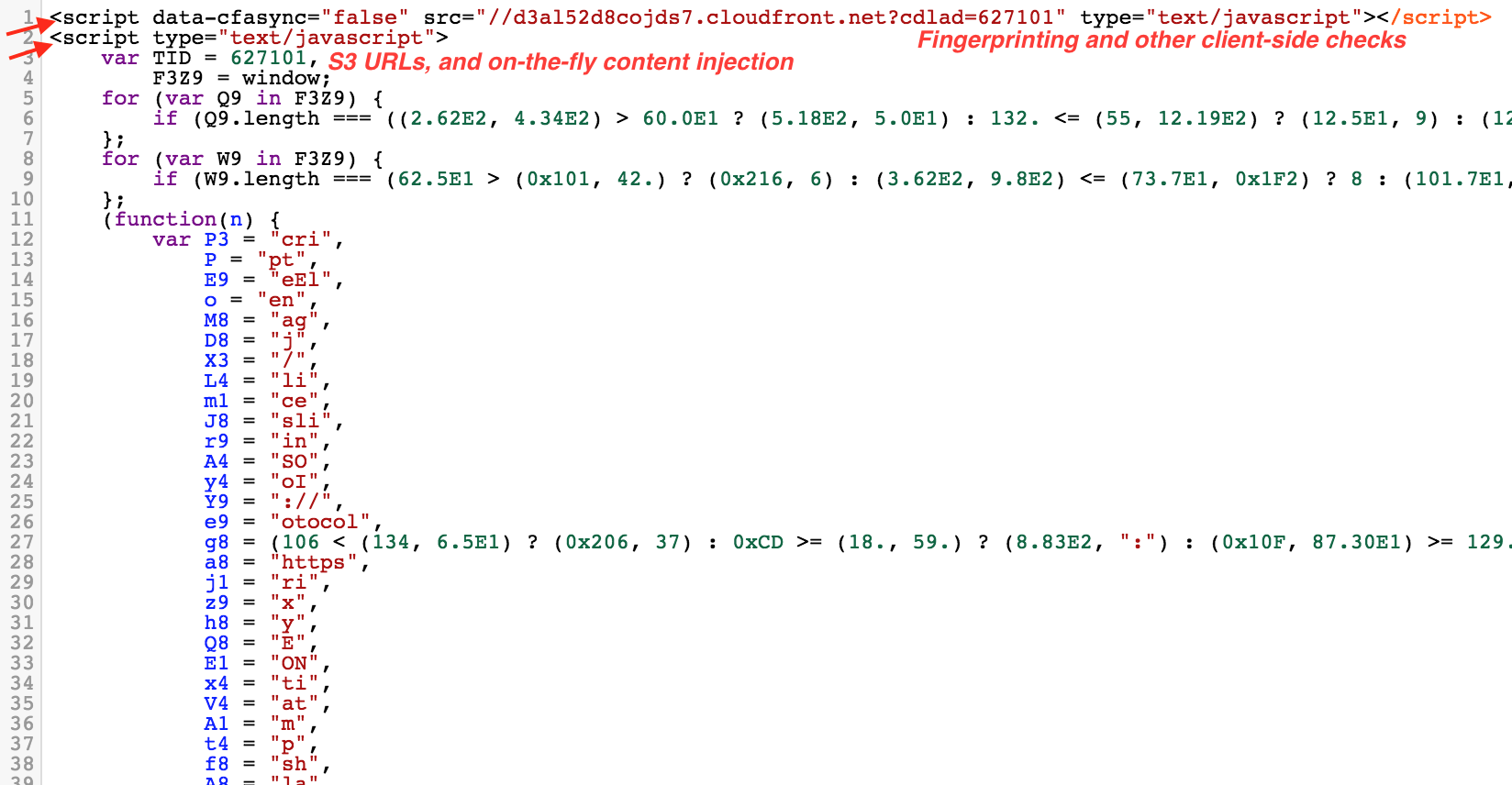
The obfuscated script above contains an algorithm to generate future Amazon S3 URLs, but the buckets are only created for the next 3-5 days.
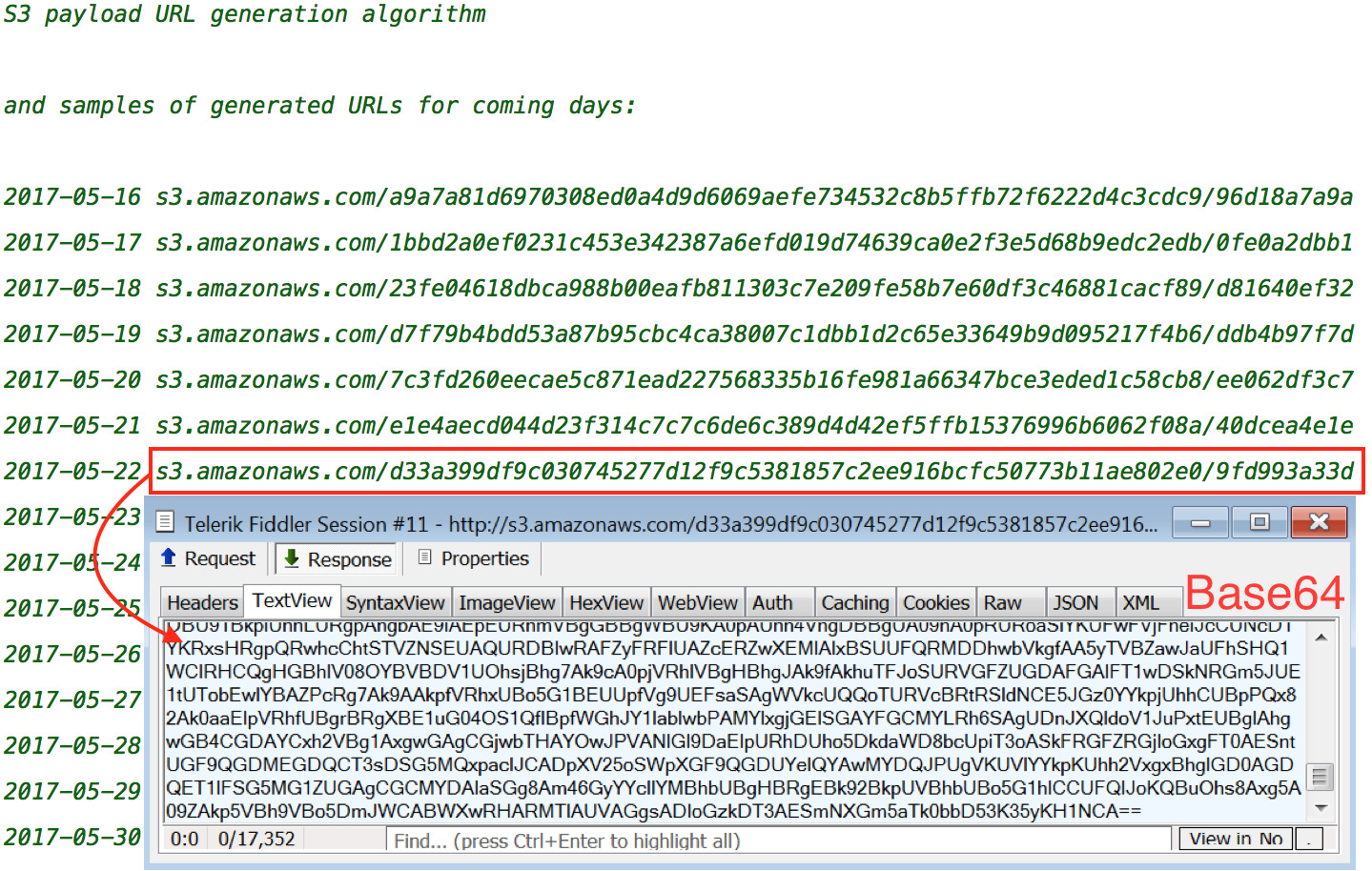
Each bucket contains a base64 encoded blurb which decodes to the current cloudfront.net subdomain:
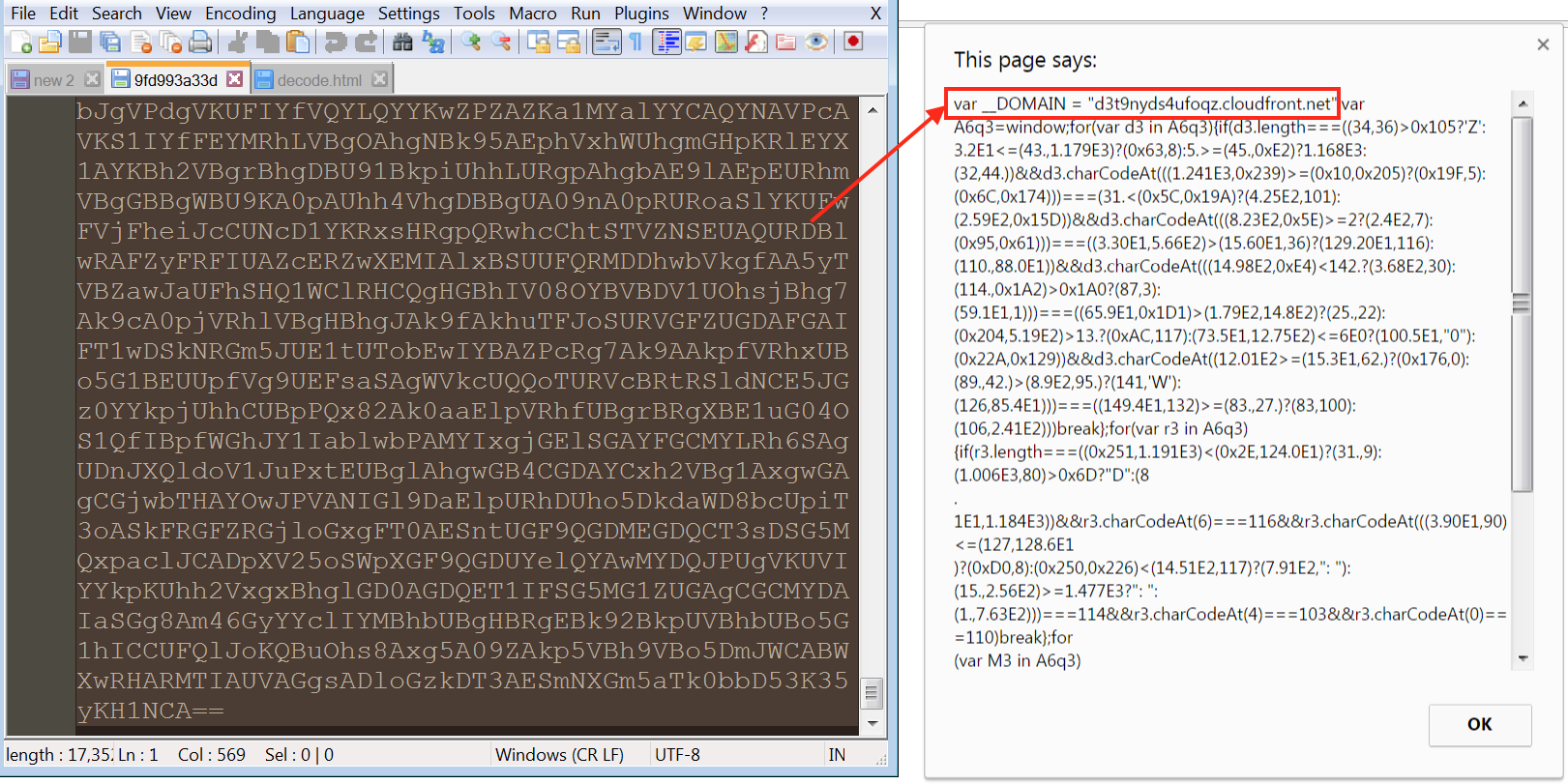
We have many examples of these cloudfront.net subdomains (leveraging the Amazon’s Content Delivery System, Amazon CloudFront CDN) seen as a referrer to RoughTed domains in our telemetry as well:
Refer: dh0uktvqfaomb.cloudfront.net/br?tid=651488 -> trandsey.info/?&pid=6&tid=651488&status=4&subid=0&info={redacted}.&v=1.1.0.1&_=1490387450476 Fingerprinting and ad-blocking evasion techniques
There’s more within this code and it has been raising eyebrows for its invasive nature, in particular for its use of fingerprinting techniques, in that case, ‘canvas fingerprinting’.
We can see it below again in a slightly different format (admvn.js) used by the URL shortener site adf.ly and redirecting users to a RoughTed domain (somethodox.info):
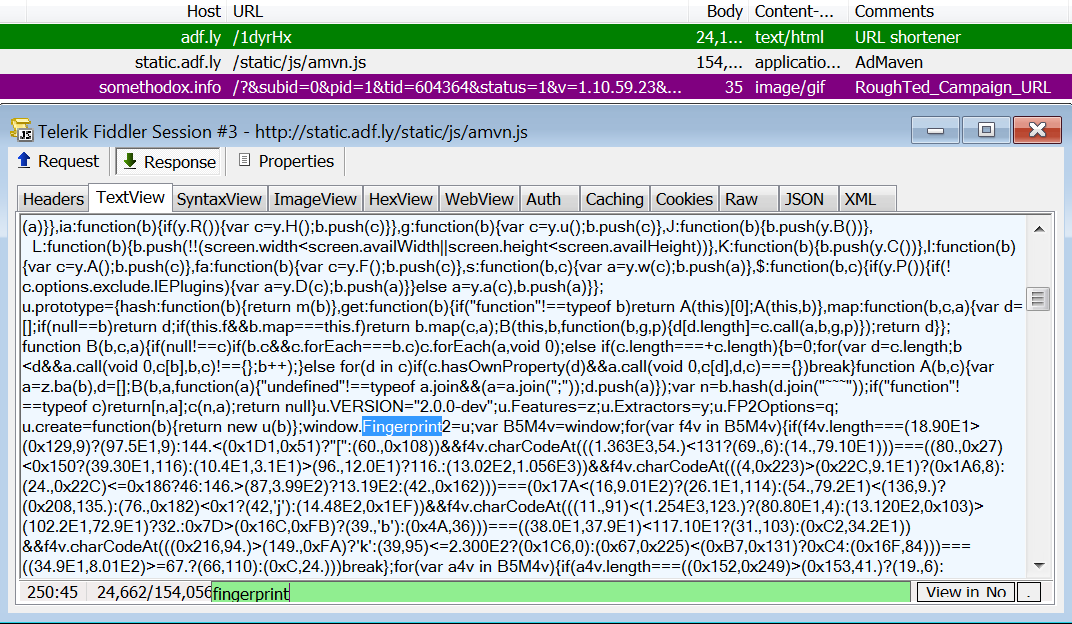
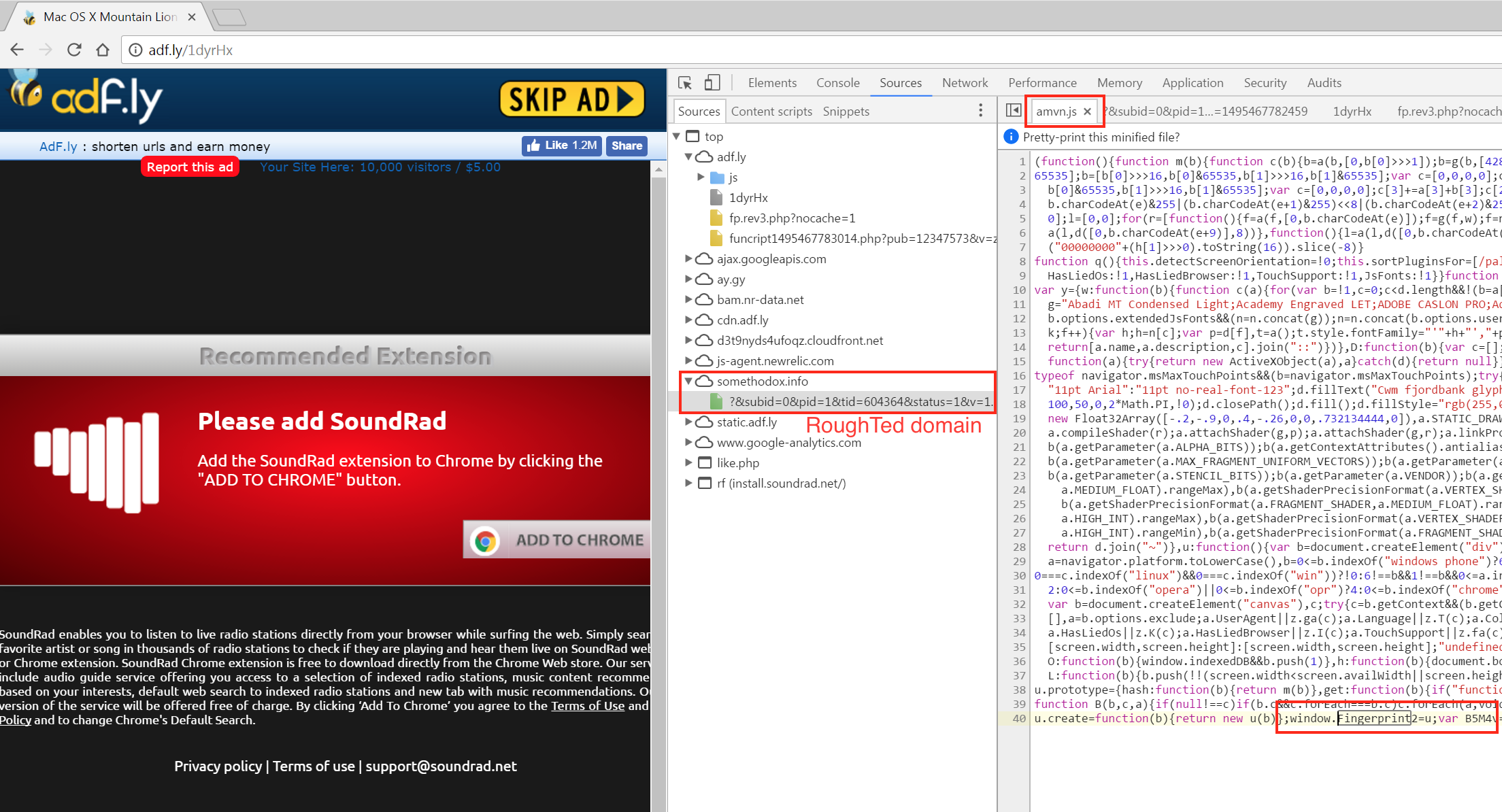
The point is to profile users with great granularity and identify those that may be cheating the system by lying about their browser or geolocation.
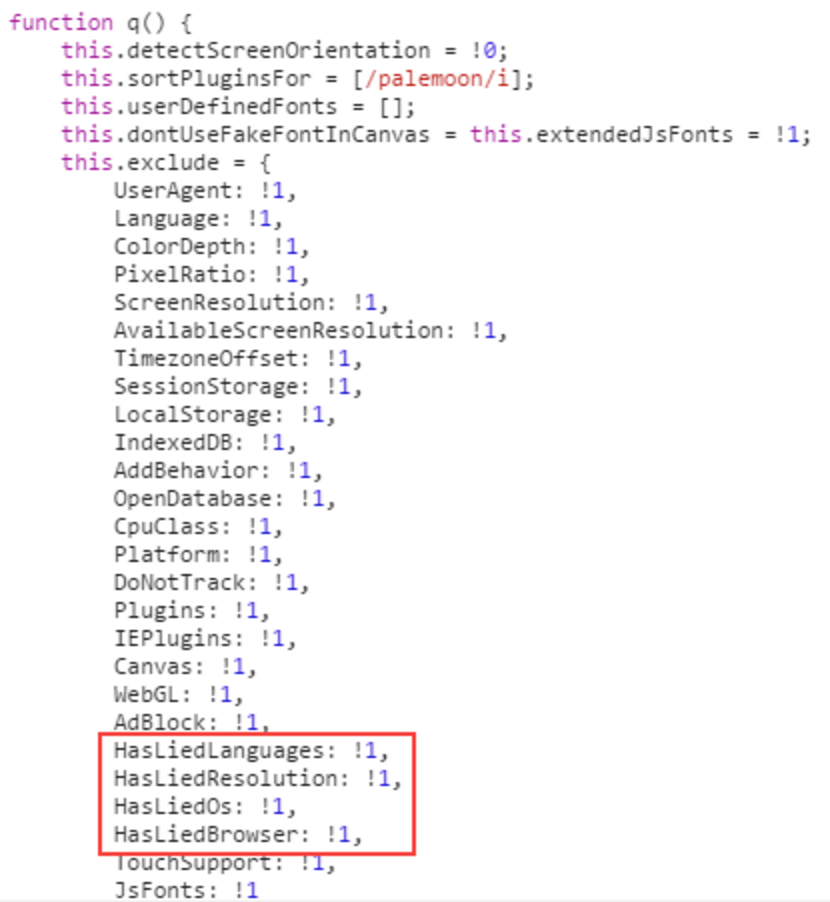
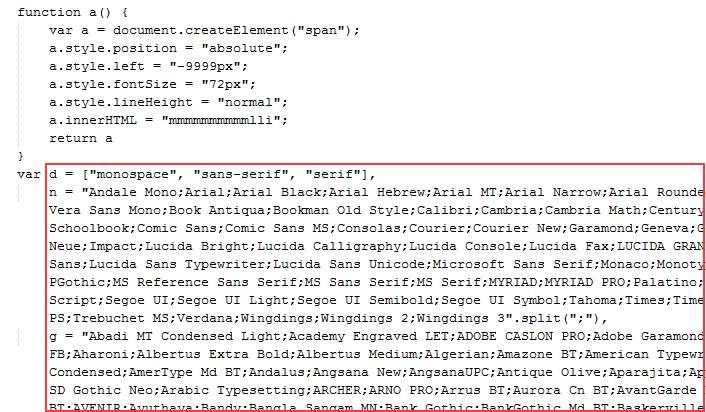
Typically the User-Agent string can determine a visitor’s OS and browser but it’s trivial to fake the UA and lie to the server. One clever alternative is to look for installed fonts since they are specific to certain operating systems, i.e. a Mac user will have different fonts than a Windows user (thank you Manuel ‘The Magician’ Caballero for pointing out this trick).
Another interesting aspect is that redirections to RoughTed domains seem to happen even to those running ad-blockers and that was reported by users of Adblock Plus, uBlock origin or AdGuard.
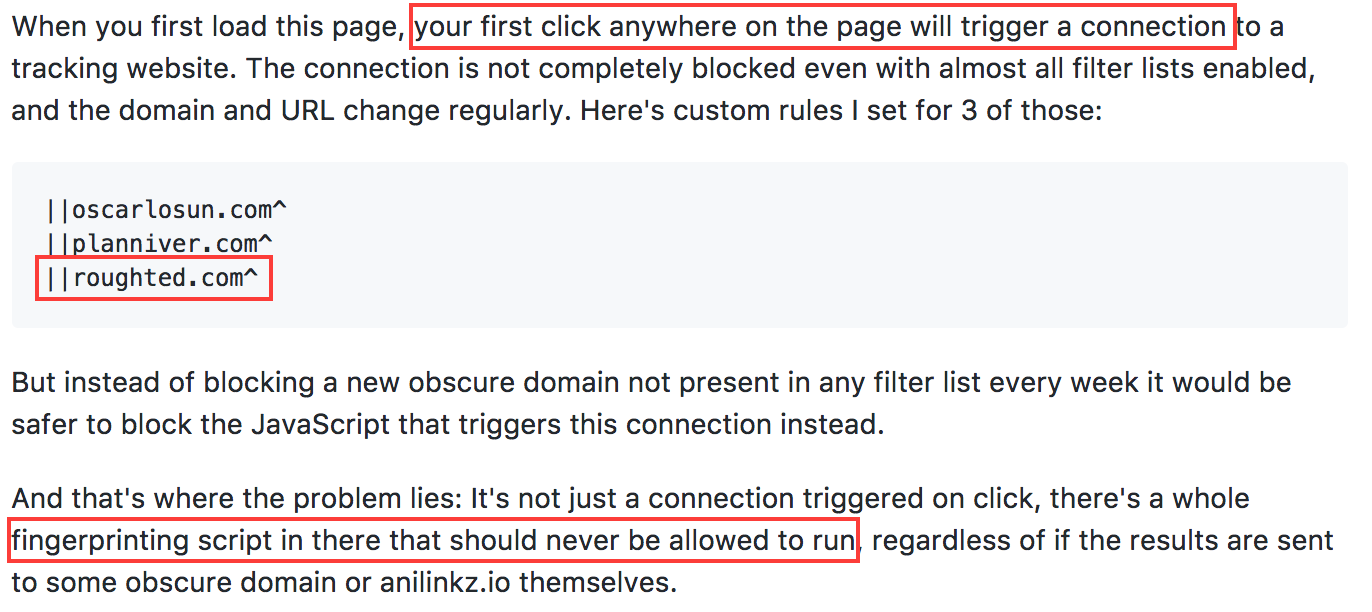
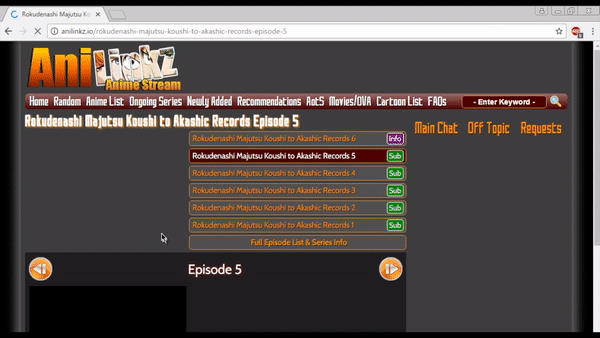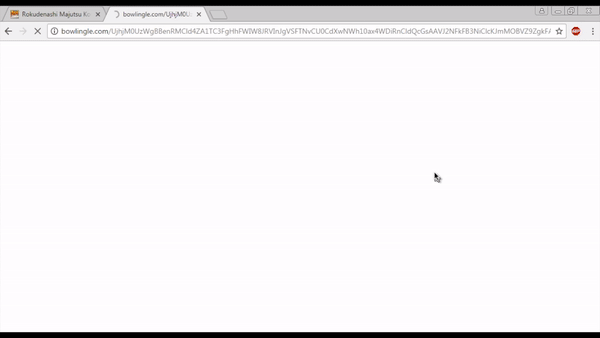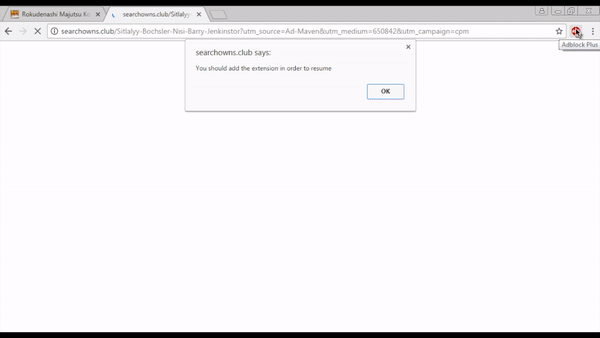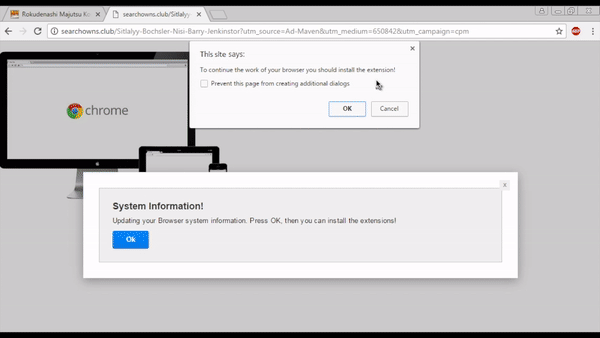
The animation below shows a redirection to one of the RoughTed gates that bypass the ad blocker in Google Chrome (ABP is shown installed and activated at the top right) and ultimately pushes a bogus Chrome extension. All a user has to do is click anywhere on the first page they visited and their browser will become hijacked.
Something for everyone
This malvertising campaign is quite diverse and no matter what your operating system or browser are, you will receive a payload of some kind. Perhaps this should be something for publishers to have a deep hard look at, knowing what they may be subjecting their visitors to if they decide to use those kinds of adverts.Adware for Mac
This is a fake Flash Player update that targets Mac users and tricks them into believing that the file comes from Apple. As a rule of thumb, you should really only download software updates from the original manufacturer, not some third-party. Unfortunately, crooks can easily create deceiving pages or scare users into installing a fraudulent piece of software.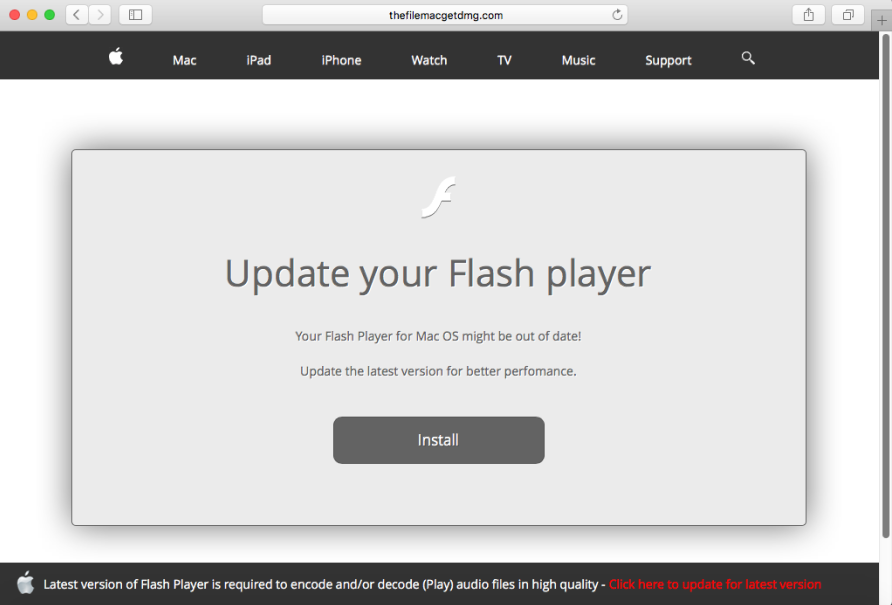
Traffic view
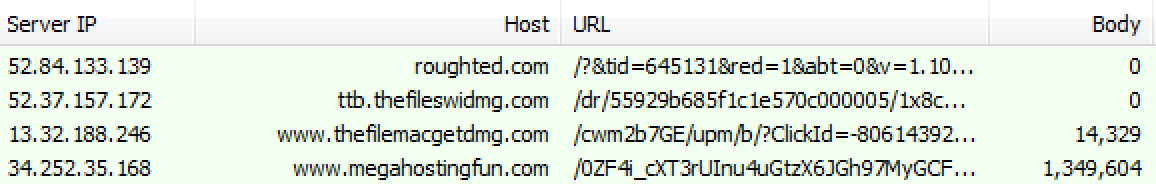
PUPs for Windows
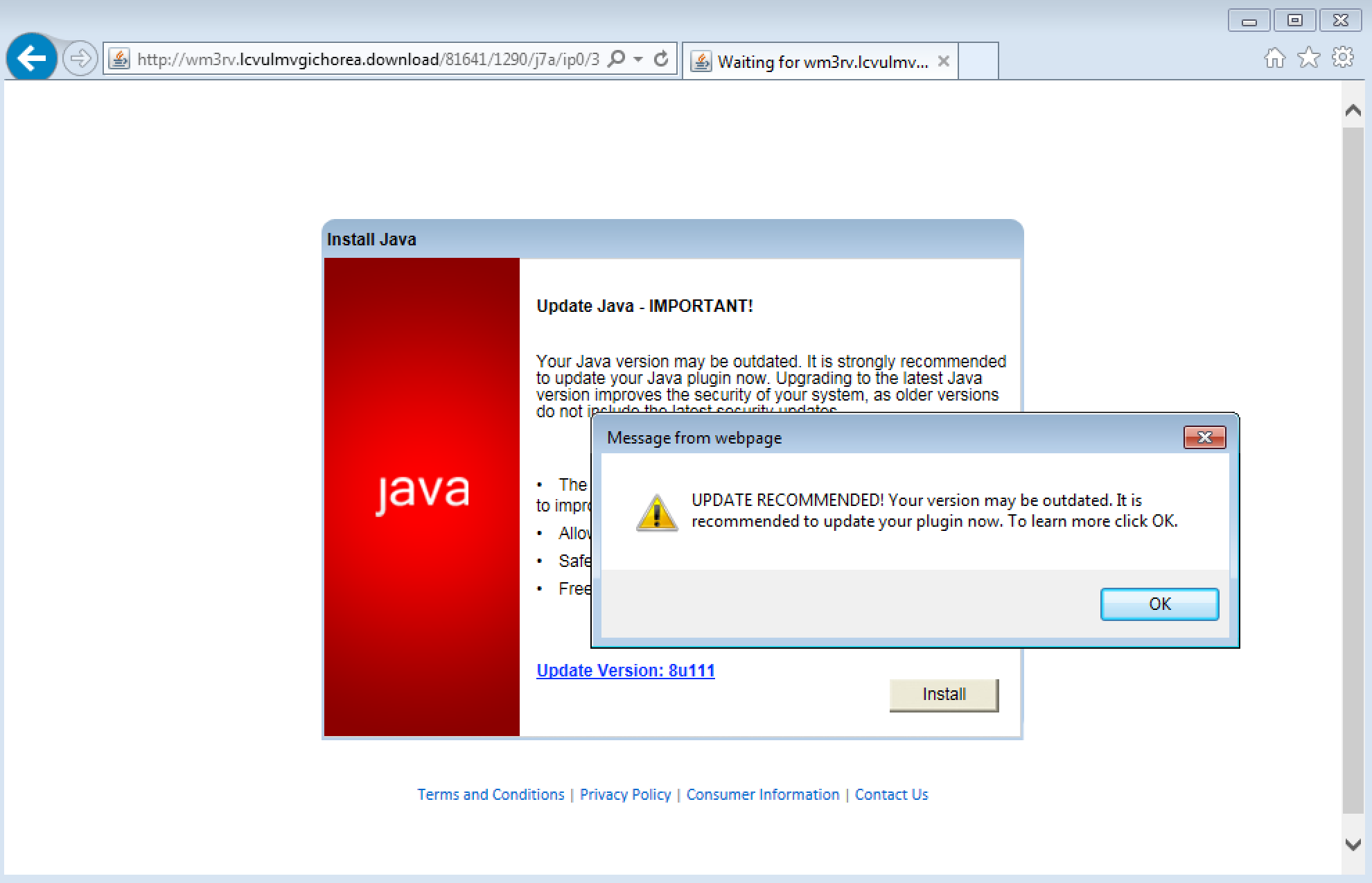
There are countless fake updates for Flash, Java, not to mention all those ‘special’ codecs for Windows. The following page urges users to install a Java update which is laced with adware. When it comes to Java, it’s usually better not having it in the first place, let alone installing some shady updates.
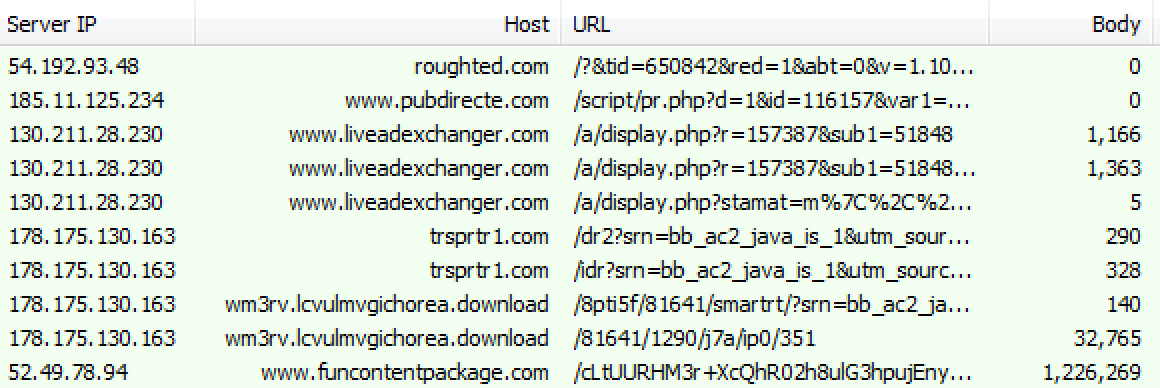
Traffic view
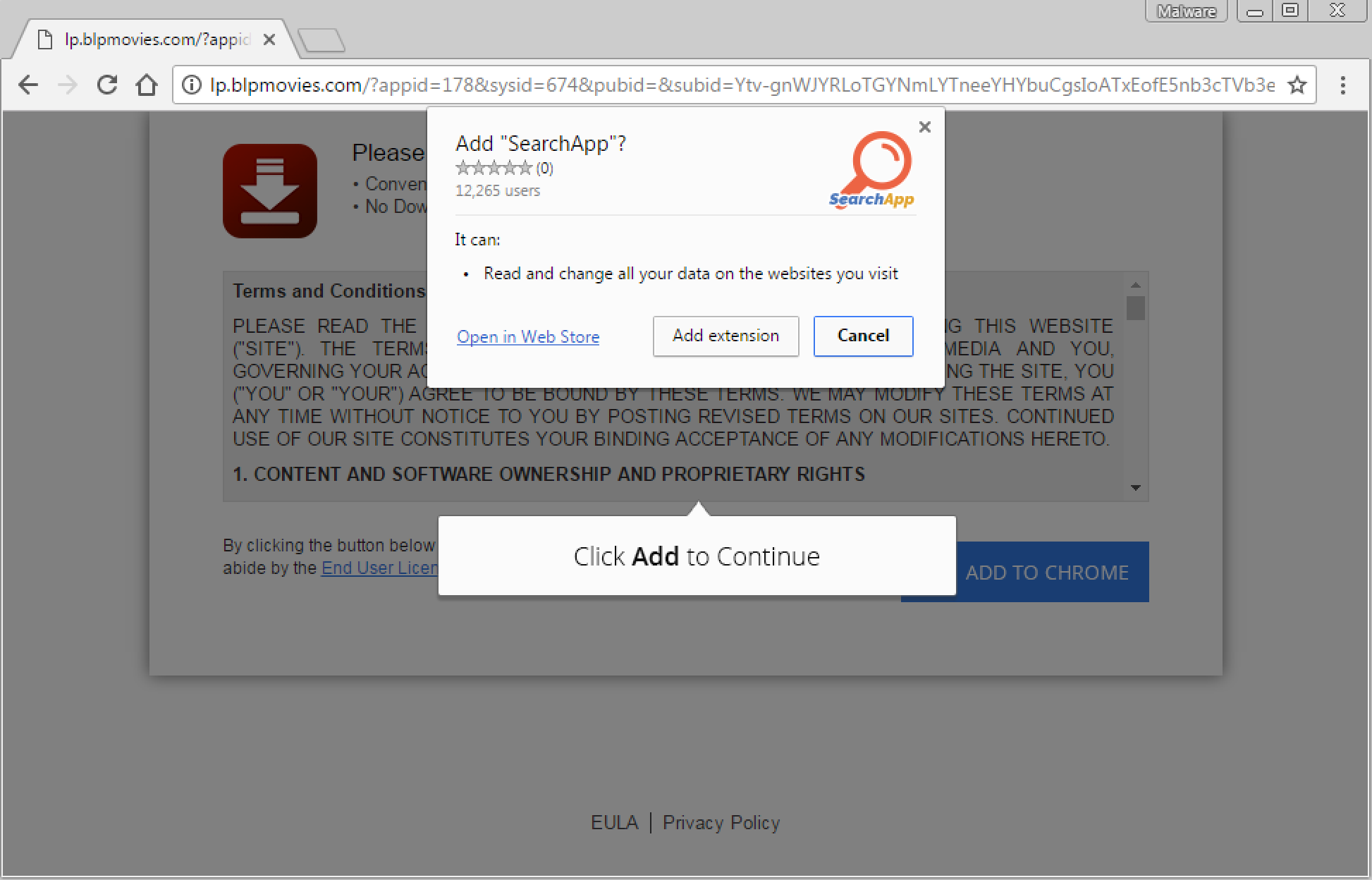
Rogue Chrome extensions
There is no question that Chrome is one of the safest browsers but unfortunately, malware purveyors and other ill-intent advertising companies are aggressively pushing rogue extensions that can collect or even modify the data on the sites you visit. Malvertising is a prime distribution method for bogus Chrome extensions which are pushed in a forceful way, leaving users little choice but to install them, in some cases.
Traffic view
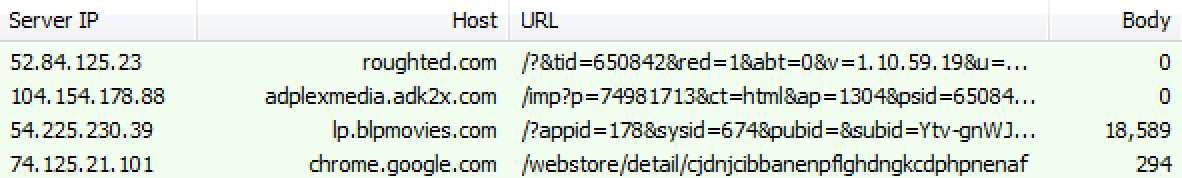
Undesired redirections to iTunes/app store
There is a large quantity of ‘free’ apps out there, both for iOS and Android and their business model is either via in-app adverts or add-ons you can purchase. Some apps go one step too far by making the game too hard to beat without buying a certain item (this is also known as ‘pay-to-win’). But after all, it is up to users to make that choice to download those apps and opt for such purchases.
However, malvertising murks the waters by doing some automated redirections to some ‘random’ apps and generating commissions for each install.
Traffic view
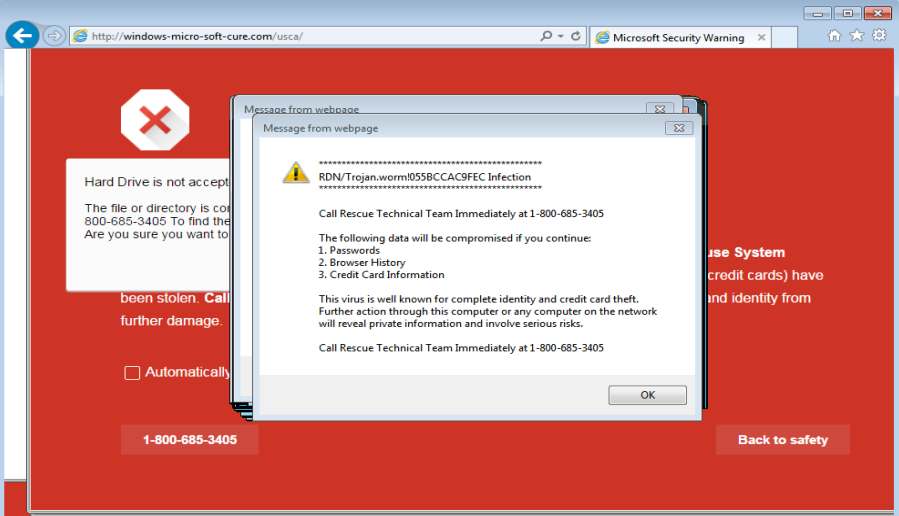
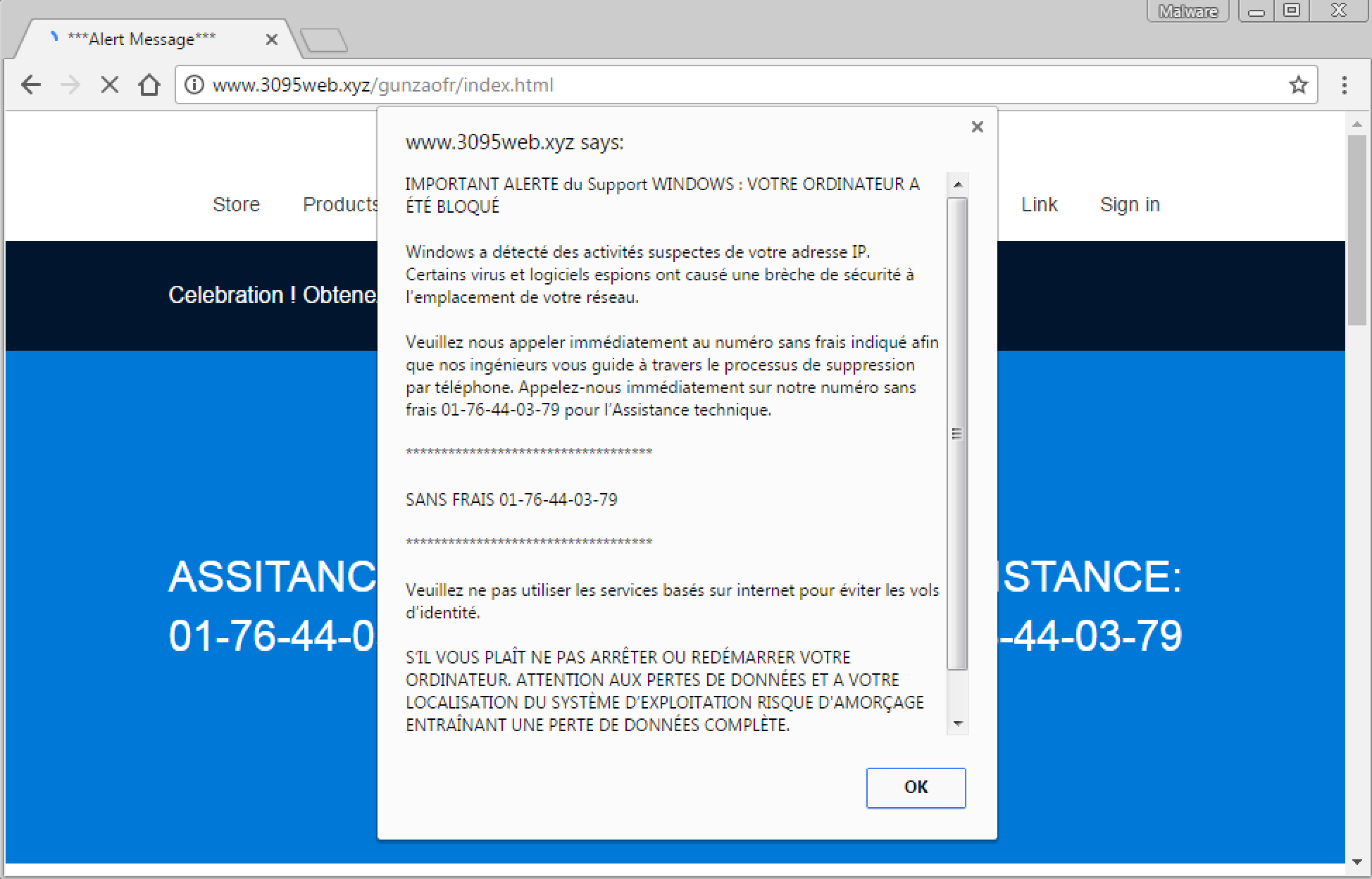
Tech support scams
Tech support scams have long been feeding off malvertising and targeting many different countries. Therefore it’s not surprising to see cases here via RoughTed as well.
Traffic view
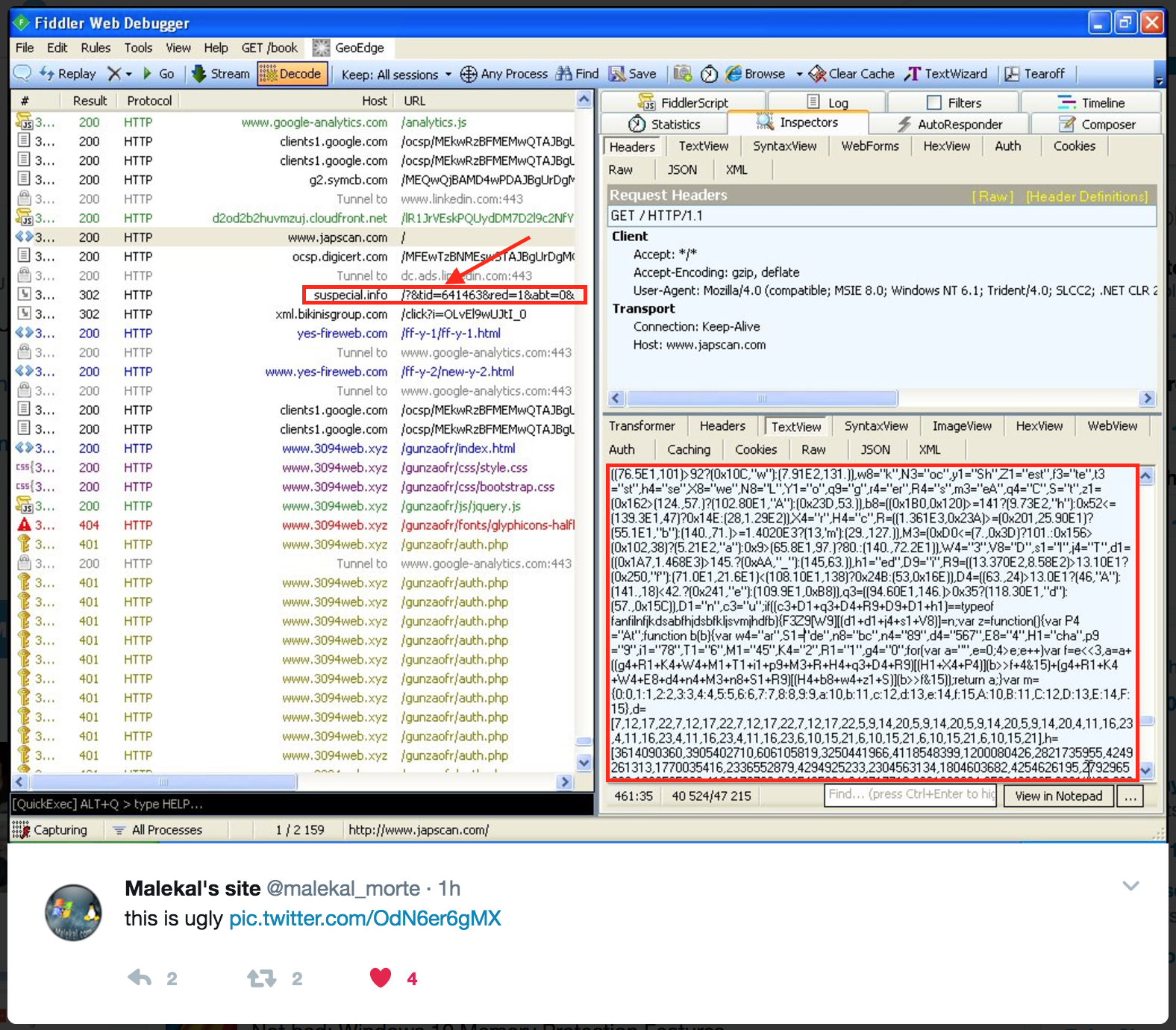
Security researcher Malekal tweeted about a Tech Support Scam (TSS) campaign targeting French people. He points at the heavily obfuscated code and we can spot a RoughTed domain (suspecial.info) in his screenshot within the HTTP traffic.
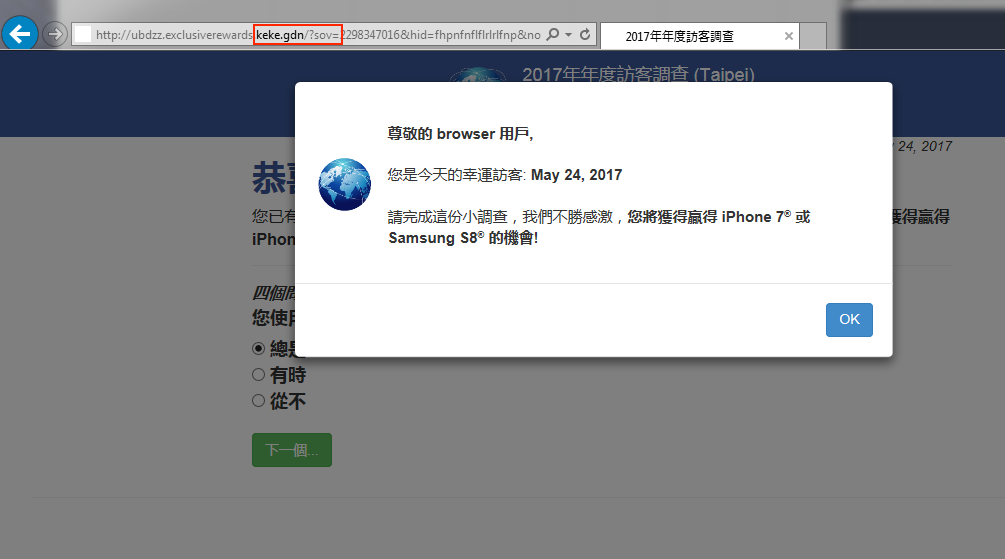
Surveys and other scams
Fake surveys or lottery pages are also common place via malvertising. In this particular sequence, we ran into NoTrove (a campaign first reported by RiskIQ).
Traffic view
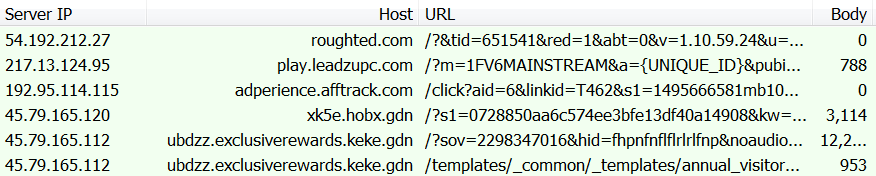
Exploit kits
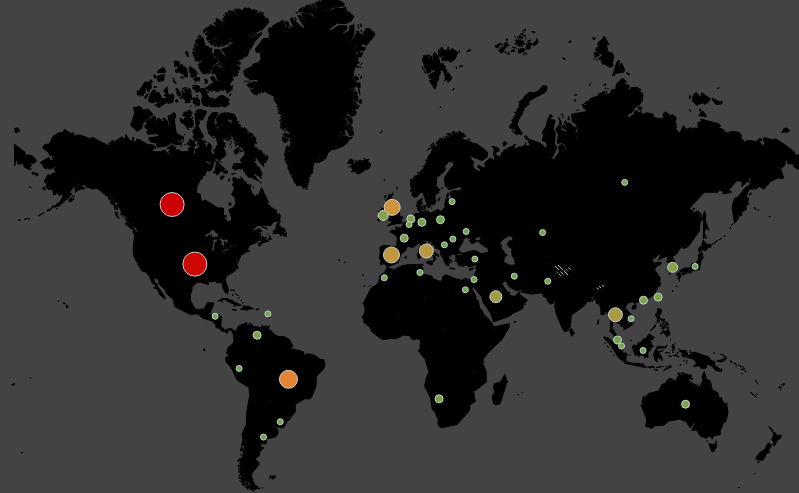
According to our telemetry records, the majority of victims impacted by exploit kits via the RoughTed malvertising campaign were in the US and Canada, followed by the U.K., Italy, Spain, and Brazil.
RIG EK
One very active malware campaign as of late is known as “Much of the upstream traffic comes from adult portals and popunder ad networks. Here you can see RoughTed involved in the ad call and chain via interesting multi-step hops leading to the Seamless campaign.
If you want to check the full redirection flow, please click here.
Magnitude EK
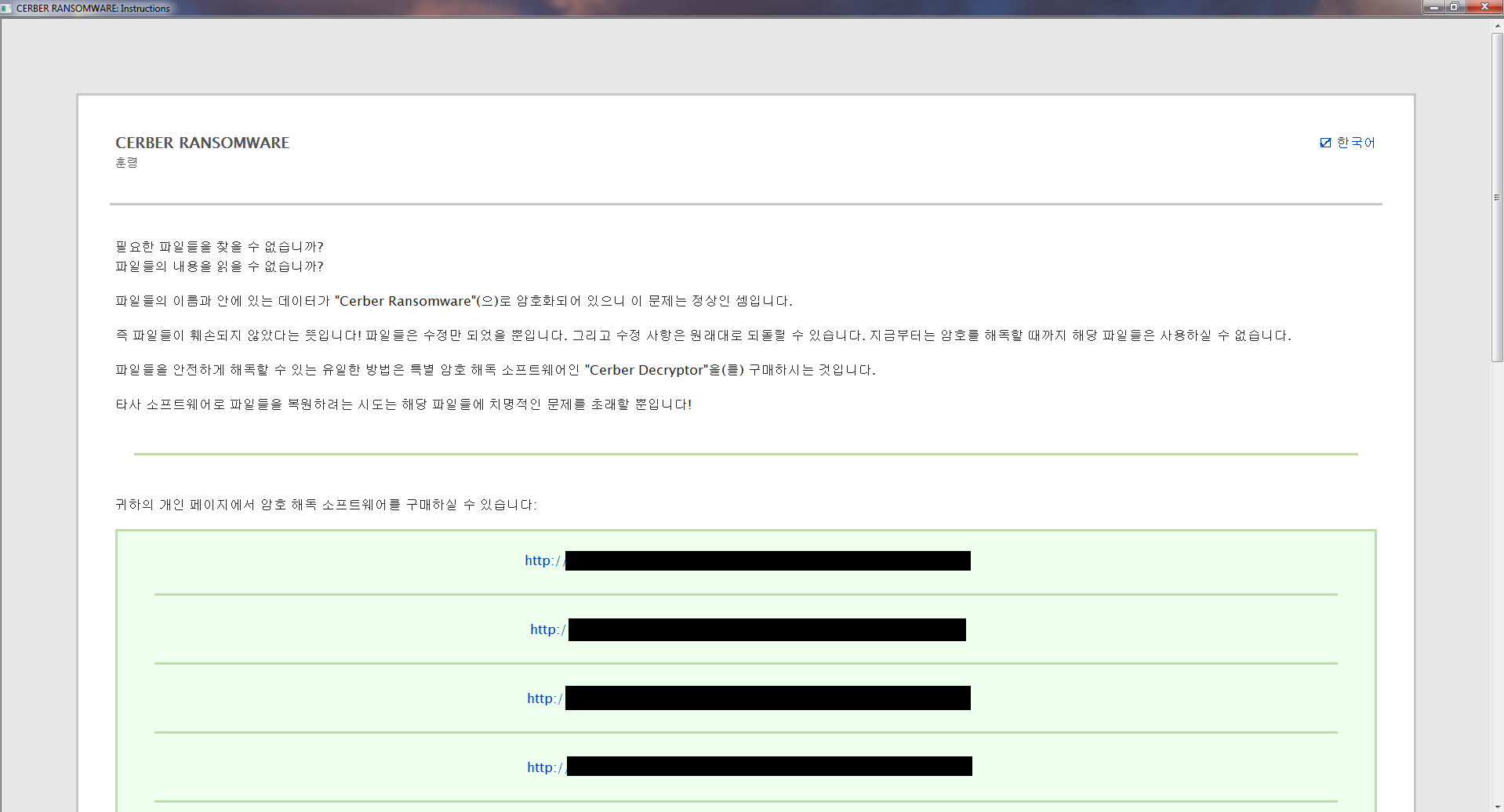
Magnitude EK has long been faithful to the Cerber ransomware as its dropped payload of choice. The bulk of infections are happening in South Korea, some in Taiwan and Hong Kong, and curiously, a few in Italy. The screenshot below is an example of a Cerber infection on a Korean user via the Magnitude exploit kit.
Traffic view
Same old, same old
Malvertising may look easy on the surface but is actually a much more complex and deep-rooted issue. We all know that it’s there and whenever a big case is uncovered, ad networks (and publishers) are blamed and it somewhat taints their brand for a little while.
But for the most part, malvertising continues unabated, especially with certain providers. The response from end users has traditionally been to gravitate towards ad-blockers as a means to avoid getting infected or bothered by obnoxious adverts.
Naturally, this has caused a similar knee-jerk reaction by some publishers and ad companies to fight back in various ways to protect their business. The rationale behind it is that people shouldn’t be getting free content that costs them money to come up with and host.
The use of dynamically created scripts to perform redirections that bypass ad-blockers are clever in many ways. For one, when a publisher includes the code on their site, it is unique to them as it is generated in their own dashboard, and by the same token, it is less likely to be detected. The script itself pulls data from a new URL every day which means blocking new domains is truly a cat and mouse game that guarantees a sufficient enough up time to serve up ads.
It becomes a real issue when this ad-supported content pushes scams or malware, even to those running an ad-blocker. At this point, one should ask themselves who really is responsible: ad networks (which are fending for themselves) or publishers (and site owners) that knowingly expose their visitors to nefarious code for the sake of ad revenues.
Thanks to Denis from Sucuri for sharing his insights into injected adverts in personal websites.
Indicators Of Compromise (IOCs)
Regex to detect RoughTed campaign
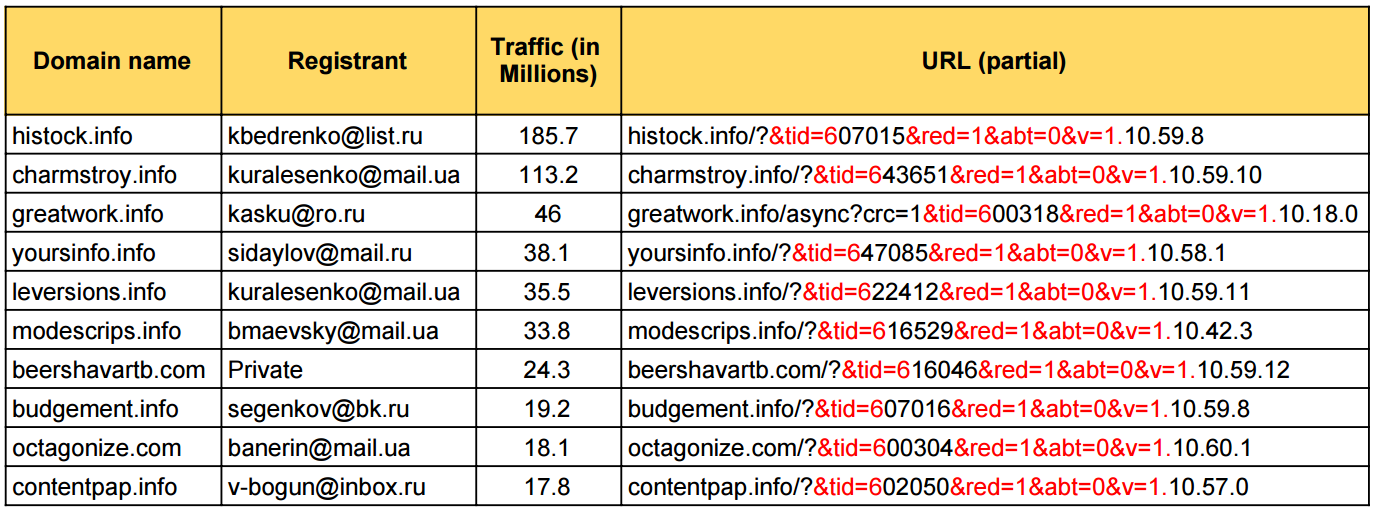
&tid=6[0-9]{5}&(status|red)=[0-9]{1,2}&(info|ref|subid|abt|v)Top RoughTed domains (by traffic)
histock.info charmstroy.info greatwork.info yoursinfo.info leversions.info modescrips.info beershavartb.com budgement.info octagonize.com contentpap.info
A longer list can be found here.
Mac PUP (FLVPlayer.dmg)
5170de1236854a73fa4c964044347142788a1d89adfa7f99704fc661620a9bd1
Windows PUP (VideoPlayerSetup.exe)
4ac4e1ebb3b51406a10f3826e048e639b1b473d53e42877bc3fef4455cb99bdc
Chrome extension (ABP bypass)
chrome.google.com/webstore/inlineinstall/detail/oihncglcaajcdibgcmdeioodpkpnnafn
Chrome extension (SearchApp)
chrome.google.com/webstore/detail/cjdnjcibbanenpflghdngkcdphpnenaf
iTunes redirection
itunes.apple.com/app/apple-store/id1095254858?mt=8
Tech support scam
windows-micro-soft-cure.com 3095web.xyz/gunzaofr/index.html
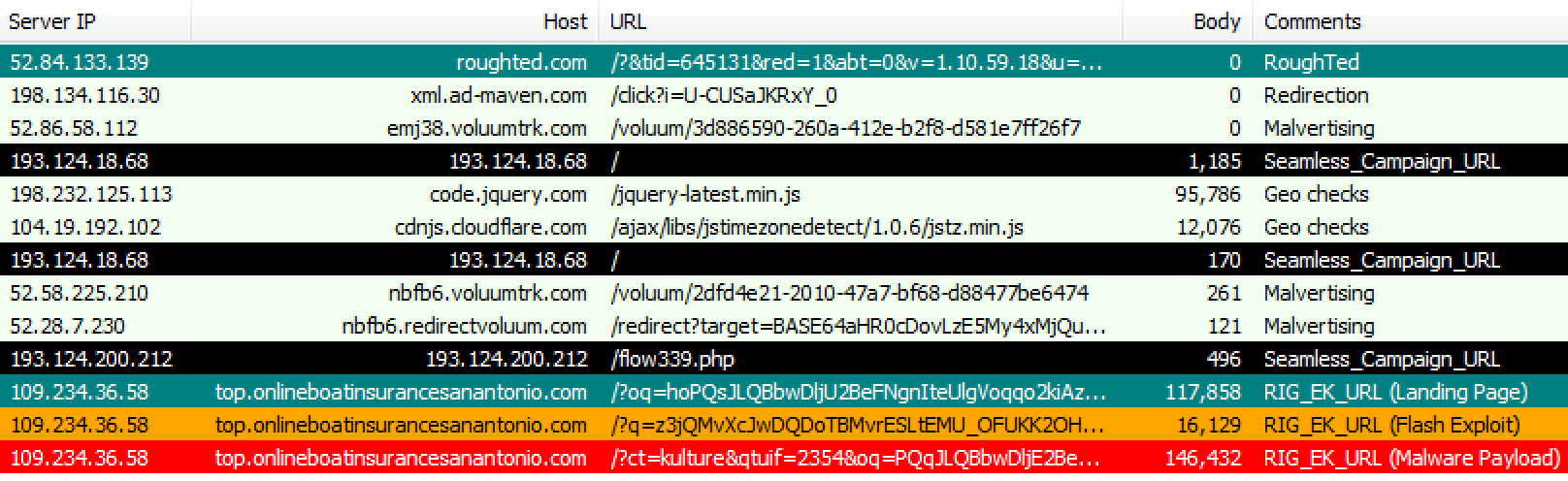
RIG EK
Method,IP address,Domain name,Comments 52.84.133.139,roughted.com,RoughTed 198.134.116.30,xml.ad-maven.com,Redirection 52.86.58.112,emj38.voluumtrk.com,Malvertising 52.28.7.230,nbfb6.redirectvoluum.com,Malvertising POST,193.124.18.68,193.124.18.68,Seamless_Campaign_URL 52.58.225.210,nbfb6.voluumtrk.com,Malvertising 193.124.200.212,193.124.200.212,Seamless_Campaign_URL 193.124.18.68,193.124.18.68,Seamless_Campaign_URL 109.234.36.58,top.onlineboatinsurancesanantonio.com,RIG_EK_URL (Flash Exploit) 109.234.36.58,top.onlineboatinsurancesanantonio.com,RIG_EK_URL (Landing Page) 109.234.36.58,top.onlineboatinsurancesanantonio.com,RIG_EK_URL (Malware Payload)Ramnit: cc4c5eabb76ebca1bc3af1d8e8a6629e72164f9ae0fc61287592548288937220
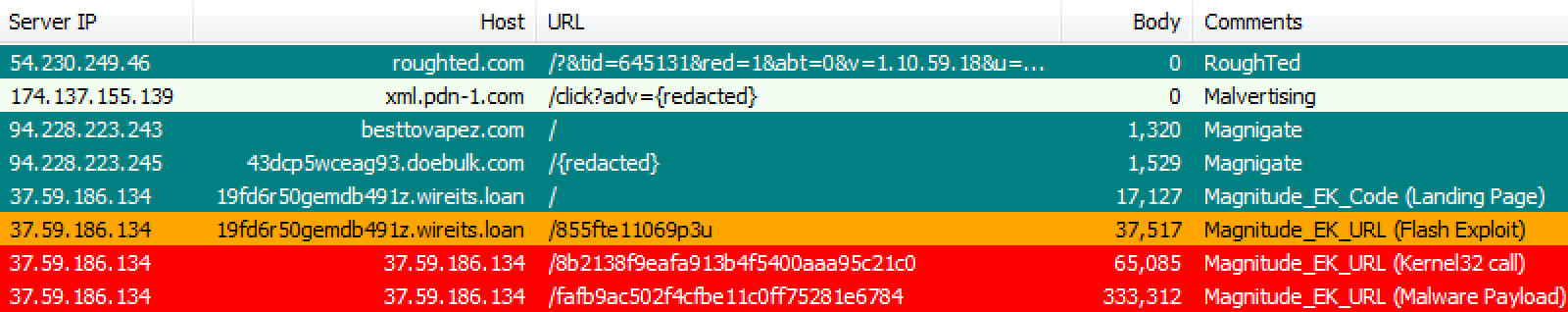
Magnitude EK
Method,IP address,Domain name,Comments 54.230.249.46,roughted.com,RoughTed 174.137.155.139,xml.pdn-1.com,Malvertising 94.228.223.243,besttovapez.com,Magnigate 94.228.223.245,43dcp5wceag93.doebulk.com,Magnigate 37.59.186.134,19fd6r50gemdb491z.wireits.loan,Magnitude_EK_Code (Landing Page) 37.59.186.134,19fd6r50gemdb491z.wireits.loan,Magnitude_EK_URL (Flash Exploit) 37.59.186.134,37.59.186.134,Magnitude_EK_URL (Kernel32 call) 37.59.186.134,37.59.186.134,Magnitude_EK_URL (Malware Payload)Cerber: d9411664ad6f1451b7cbd2a9453e5824d566535bae480dfe533cda7e0bef0ae7