Whether you call it WannaCry, WannaCrypt, WCrypt, Wanacrypt0r, WCry, or one of the other names currently vying for the “call me…
Month: May 2017
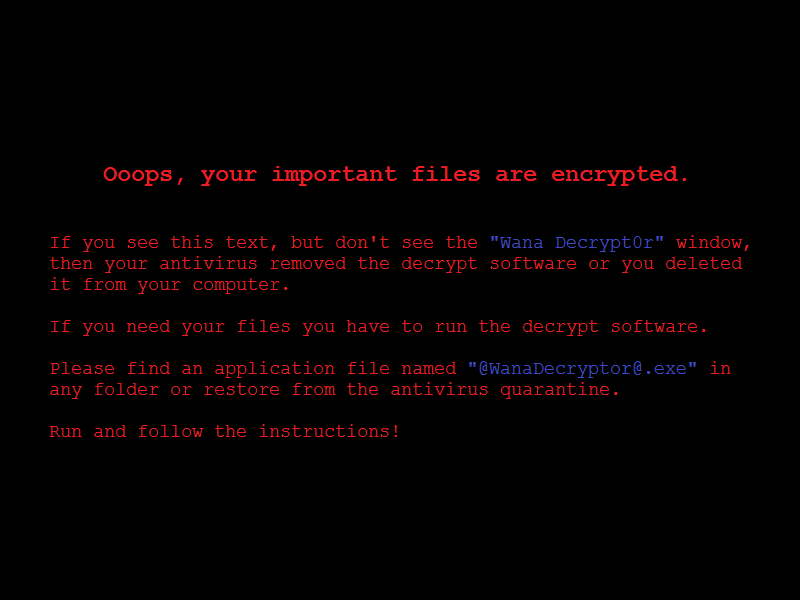
The worm that spreads WanaCrypt0r
Something that many security researchers have feared has indeed come true. Threat actors have integrated a critical exploit taking advantage of…
WanaCrypt0r ransomware hits it big just before the weekend
UPDATE (as of 5/18/17): UPDATE (as of 5/17/17): Reports of two massive, global ransomware attacks are dominating the news. As workers…
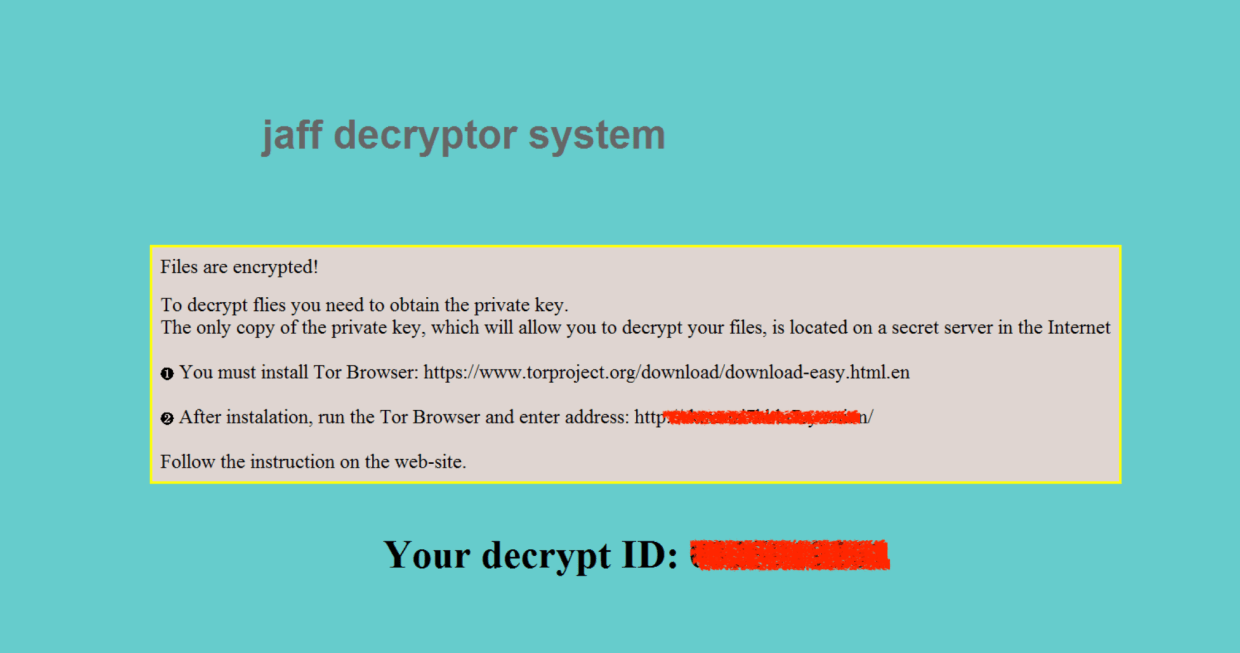
New ‘Jaff’ ransomware via Necurs asks for 2 BTC
There is yet another ransomware on the block, but contrary to the many copycats out there this one appears to be…
Adware the series, part 3
In this series of posts, we will be using the flowchart below to follow the process of determining which adware we are dealing…
HandBrake hacked to drop new variant of Proton malware
Last year, the Transmission torrent app was hacked not just once, but twice, to install the KeRanger ransomware and, later, the…
A week in security (May 01 – May 07)
Last week, we reported about that fake Google Docs app in real time as it wrecks havoc among GMail users worldwide….
Snake malware ported from Windows to Mac
Snake, also known as Turla and Uroburos, is backdoor malware that has been around and infecting Windows systems since at least…
Why you don’t need 27 different passwords
Passwords. The bane of modern existence. To celebrate this nuisance, the holiday gods have given us World Password Day, where thousands…
OWASP top ten – Boring security that pays off
There’s a lot of very unique, creative, and devastating cyber threats out there. The first inclination of a defender is to…