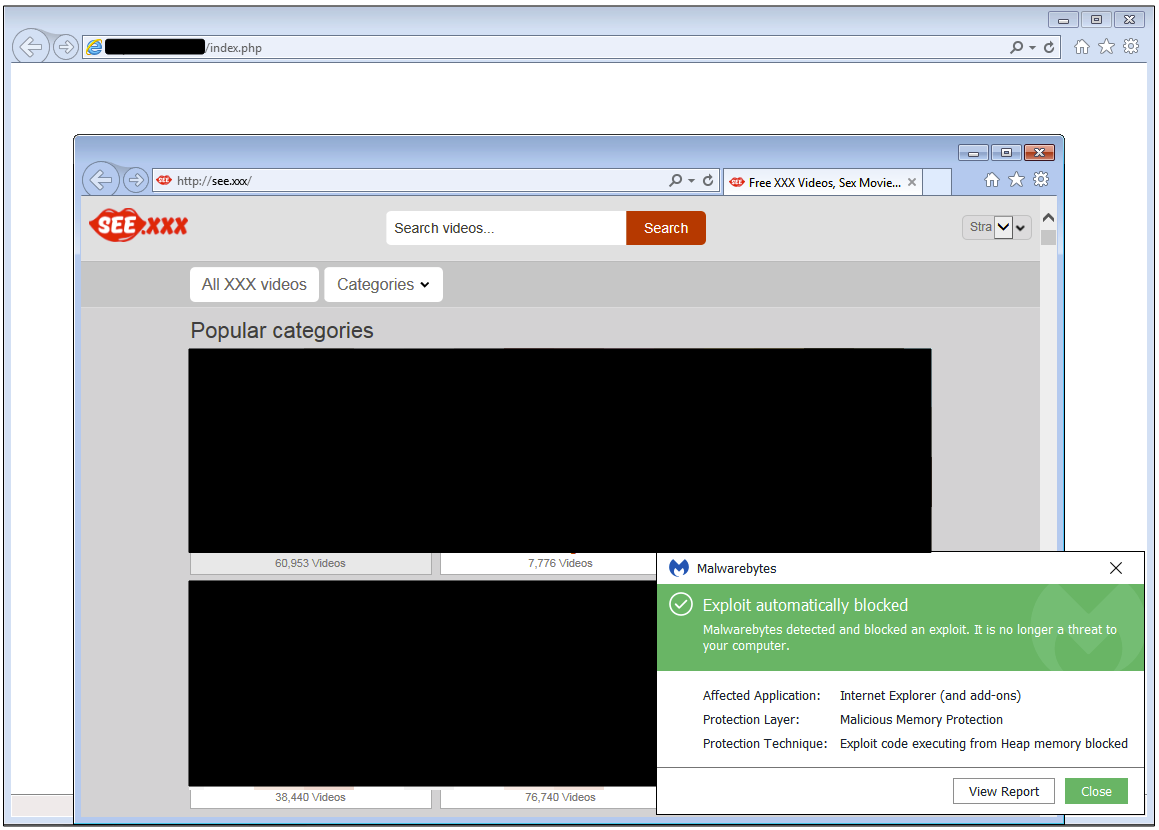
Over the last few days we have observed an increase in malvertising activity coming from adult websites that have significant traffic (several million monthly visits each). Malicious actors are using pop-under ads (adverts that load in a new browser window under the current active page) to surreptitiously redirect users to the RIG exploit kit.
This particular campaign abuses the ExoClick ad network (ExoClick was informed and took action to stop the fraudulent advertiser based on our reports) and, according to our telemetry, primarily targets Canada and the U.K.. The ultimate payloads we collected during this time period were all the Ramnit information stealer (banking, FTP credentials, etc.) which despite a takedown in 2015 has rebounded and is quite active again.
Pop-under ads and TDS
Pop-under ads are usually triggered when a user clicks on an item on the site they are browsing. In this particular example, clicking on one of the category thumbnails launches the pop-under window behind the main page.
The first stage redirection includes a link to tds.tuberl.com within two different JavaScript snippets. This Traffic Distribution System (TDS) mostly loads benign adult portals/offers via ExoClick. The actual malvertising incident takes place next with a 302 redirect to a malicious TDS this time, which performs some geolocation fingerprinting and checks the upper referer before loading the RIG exploit kit.
Traffic overview:
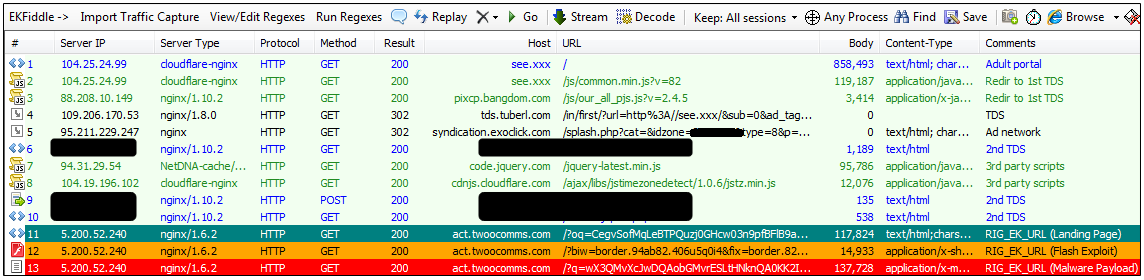
Redirection chain:
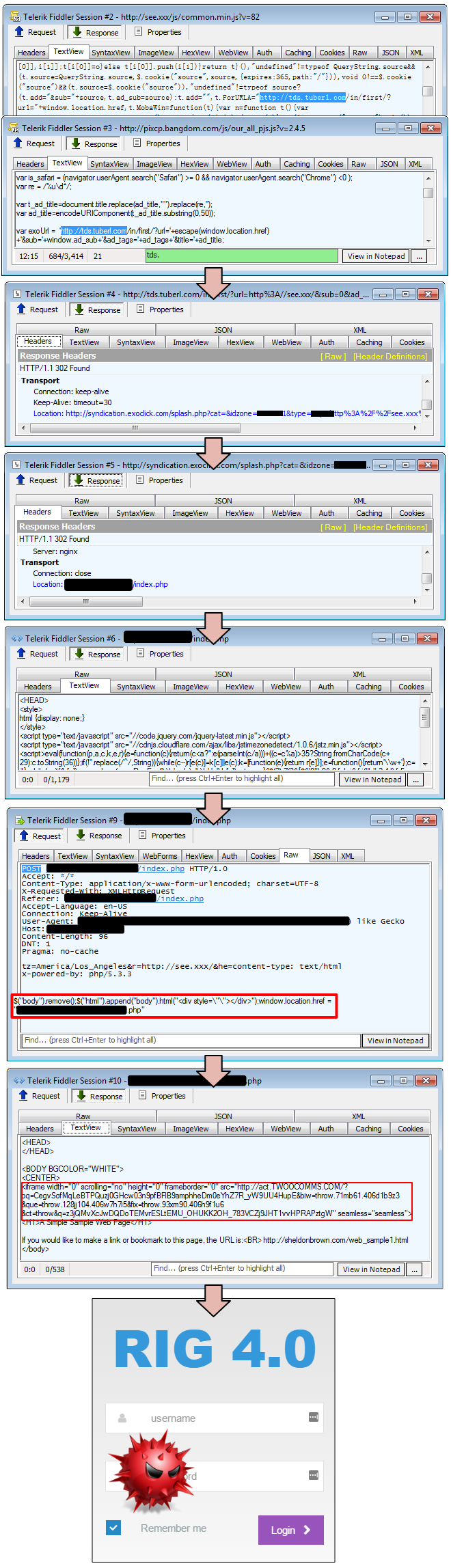
Figure 3: TDS redirection based on the user’s geolocation
We noted the same attack pattern with several other adult portals using the malicious TDS mentioned above to load RIG EK:
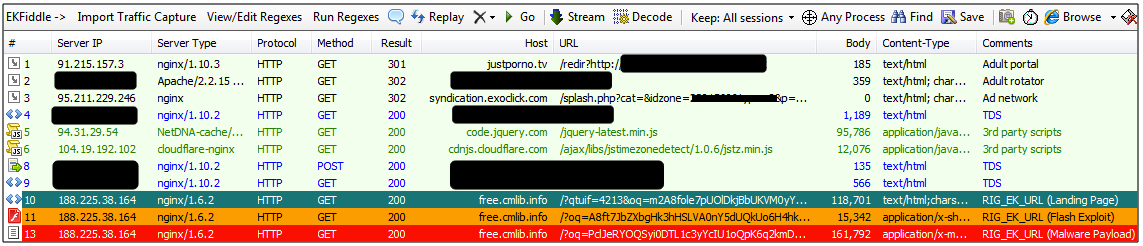
Ramnit going after Canada and the U.K.
The payloads we collected via our honeypot were all the Ramnit Trojan, which is interesting considering the traffic flow from the TDS (Canada, U.K. being the most hits recorded in our telemetry). A report from IBM security researcher Limor Kessem in December 2015 indicated that Canada was the top target with 55% of all Ramnit activity. A follow up report from the same researcher in August 2016 showed a new wave of attacks directed this time at the U.K.
We informed ExoClick and they have been able to locate and terminate the rogue advertiser. Malwarebytes users were already protected against this distribution campaign and the Ramnit Trojan.
IOCs
Malware hashes:
53ba545c599a66a148e590b11e9cdc0d49141b03d9f870fcd52593f39bcd690d 845824afa87c0eccf25b09cbf57fbe2ab9e356b6cdbac220271e9c4e732bb174 3feb4c5198cd00361dc5631334288f9ba6a25b3d35028b0cd10f453525ff1c9e c72e3c5120e948599a2f6f215a7ef53f71763ce16303782872bab9cf5599610a be3705cf0964cebe7084439f502ae4d40fc063693be44fbe54fe7a9f8ae180df 228af3aa07a2c37badf83cdd552710434601d8f3abf60df8d8264cdf3f694d70
RIG EK domains:
set.designervintagejewelry.com cxz.suttonsite.com rew.lafontant.services new.serviceslafontant.ca act.opencomputinginstitute.com free.learntoridemotorcycle.com rew.dietingplan.org gfd.dealsboy.in admin.sellsettlement.org act.loseyourweightnaturally.com acc.buycellulitetreatments.com art.joecornellweddings.com see.chairblue.com list.werledlighting.com never.alexagift.com see.aliharperweddings.com see.clicklinkto.info free.nutrangnu.com all.woodfurnituregarden.com top.villabluesteps.com act.obamapower.com new.4u-insurance.com art.carondeletevents.com add.cmlib.org far.clickbankidol.com rew.terrigenesis.com line.bermudaweddings.net rec.goldenknightsfan.com try.sjtri.com add.lvgoldenknightsfan.com free.cmlib.info act.twoocomms.com
RIG EK IPs:
188.225.38.209 188.225.38.186 188.225.38.164 188.225.38.131 5.200.52.240